Introduction to the YubiKey Series
Where applicable, throughout this guide, the YubiKey 5 Series, the YubiKey 5 FIPS Series, the YubiKey 5 CCN Series, and the YubiKey 5 Enhanced PIN Series are referred to collectively as the YubiKey 5 Series, because all these YubiKeys share the same hardware base and many firmware features.
Also described in this guide are the YubiKey Bio Series and the Yubico Security Key Series.
This topic introduces:
- YubiKey 5 Series
- YubiKey 5 FIPS Series
- YubiKey 5 CCN Series
- YubiKey 5 Enhanced PIN Series
- YubiKey Bio Series
- Security Key Series
- Firmware
For a convenient way of comparing YubiKeys in 5 Series, Bio Series, and Security Keys Series, see Yubico’s YubiKey Comparison Chart.
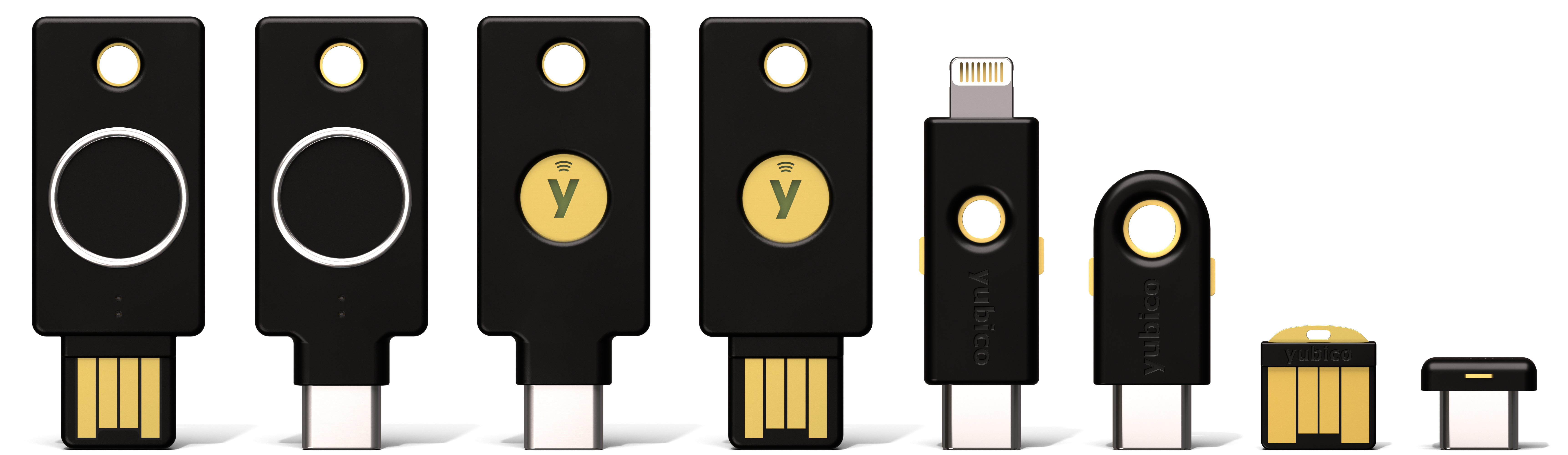
YubiKey Series Form Factors
The YubiKey Series and form factors (in order from the image) are listed in the table.
YubiKey Series
|
5 NFC
Bio
|
5C NFC
Bio
|
5C NFC
|
5 NFC
|
5Ci
|
5C
|
5 Nano
|
5C Nano
|
|---|---|---|---|---|---|---|---|---|
| Standard | USB-C | USB-A | USB-C,
lightning
|
USB-C | USB-A | USB-C | ||
| FIPS | USB-C | USB-A | USB-C,
lightning
|
USB-C | USB-A | USB-C | ||
| Enhanced PIN | USB-C | USB-A | ||||||
| CCN | USB-C | USB-A | ||||||
| Bio | USB-A | USB-C | ||||||
| Security Key | USB-C | USB-A |
Where series codes indicate an interface type. See Physical Interfaces: USB, NFC, Apple Lightning®.
- NFC - Near Field Communication
- C - USB-C connector
- Ci - Apple lightning connector
- Other - USB-A connector
For a quick start, to register your YubiKey with supported applications and services, see Set up your YubiKey
YubiKey 5 Series
The YubiKey 5 Series security keys offer strong authentication with support for multiple protocols, including FIDO2, which is the new standard that enables the replacement of password-based authentication. The YubiKey strengthens security by replacing passwords with strong hardware-based authentication using public key cryptography.
For those who just want to use a YubiKey without programming anything, the most useful part of this guide is Understanding the USB Interfaces. This topic describes how the YubiKey connects and indicates what it can connect to.
For an overview on setting up two-step verification in a typical case, see Google on using a security key for 2-step verification.
The full list of the services that work with YubiKeys is on Yubico’s Works With YubiKey page.
Most of the rest of this guide targets systems integrators, IT teams, or developers who expect to integrate support for YubiKeys into their environment.
Protocols and Applications lists the YubiKey 5 Series functionalities and capabilities by protocol:
Note
It is the firmware version that determines which of the more specialized functionalities and capabilities are available on your YubiKey. See Firmware.
Yubico Authenticator is one of the tools most commonly used to configure YubiKeys, so for a complete breakdown of Yubico Authenticator functionality by platform and connection type for each YubiKey model, see the Yubico Authenticator Functionality table.
The Yubico ykman CLI (command line interface) is another advanced cross-platform tool for advanced management and configuration of all YubiKey applications (FIDO2, FIDO U2F, PIV, Yubico OTP, YubiHSM Auth, OpenPGP, OATH, Security Domain). See the YubiKey Manager (ykman) CLI Guide.
For a list of YubiKey 5 Series specifications, see the YubiKey 5 Series Product Brief.
YubiKey 5 FIPS Series
Federal Information Processing Standards (FIPS) are developed by the United States government for use in computer systems to establish requirements such as ensuring computer security and interoperability. The National Institute of Standards and Technology (NIST) and the Canadian Centre for Cyber Security (CCCS) run the NIST Cryptographic Module Validation Program (CMVP) as a collaborative effort.
FIPS certification demonstrates that a product has gone through a rigorous audit process and adheres to a security standard that can be measured and quantified.
Many government organizations and government contractors are required to use FIPS-approved products, as are highly-regulated industries in general. Other countries also recognize FIPS 140-2. For the U.S. government, the default is that FIPS is required.
For a list of YubiKey 5 FIPS Series specifications, see the YubiKey 5 FIPS Series Product Brief.
Do You Require FIPS Keys?
If you do not have a security auditor, and/or the auditor does not have a compliance requirement, you probably do not need FIPS. The standard line of YubiKeys (the non-FIPS series) offers the same security, algorithms, and functionality. The standard line also evolves at a much more rapid pace because it does not need to complete an exhaustive validation process, which commonly takes a year or more. Yubico can release standard firmware with new features and enhancements at any time, whereas FIPS-certified products must go through the FIPS validation process every time there is a firmware change.
About the YubiKey 5 FIPS Series
The YubiKey 5 FIPS Series is FIPS 140-2 certified. It offers strong authentication with support for multiple protocols, including FIDO2, which is the new standard that enables the replacement of password-based authentication. The YubiKey strengthens security by replacing passwords with strong hardware-based authentication using public key cryptography.
The cryptographic functionality of the YubiKey 5 FIPS Series devices is powered by the YubiKey 5 cryptographic module, a single-chip cryptographic processor with a non-extractable key store that handles all of the cryptographic operations. The YubiKey 5 cryptographic module is FIPS 140-2 certified, both Level 1 and Level 2 (Physical Security Level 3).
The YubiKey 5 FIPS Series cryptographic module is a security feature that supports multiple protocols designed to be embedded in USB security tokens. The module can generate, store, and perform cryptographic operations for sensitive data. It is accessed through an external touch-button for Test of User Presence in addition to PIN for smart card authentication. The module implements the following major functions, depending on the firmware version on the YubiKey.
YubiKey 5 FIPS Series Cryptographic Module Major Functions
| Function | Firmware Versions | ||
|---|---|---|---|
| 5.7.4 | 5.4.3 | 5.4.2 | |
| Yubico One Time Password (OTP) | yes | yes | yes |
| OATH OTP authentication | yes | yes | yes |
| OpenPGP (version 3.4) | yes | yes | |
| PIV-compatible smart card | yes | yes | yes |
| FIDO Universal 2nd Factor (U2F) | yes | yes | yes |
| FIDO2 WebAuthn | yes | yes | yes |
| YubiHSM Auth | yes | yes | |
| SCP03 | yes | yes | yes |
| SCP11 | yes | ||
Note
The 5.7.4 is not a FIPS key, but it shares the cryptographic module major functions.
The YubiKey 5 FIPS Series hardware with the 5.4 firmware is certified as an authenticator under both FIPS 140-2 Level 1 and Level 2. It meets the highest authenticator assurance level 3 (AAL3) of NIST SP800-63B guidance. To use security keys from the YubiKey 5 FIPS Series as a Level 2, more stringent initialization is required than for Level 1. Guidance for Level 2 is detailed in Deploying the YubiKey 5 FIPS Series. Guidance for Level 3 is set out in YubiKey 5 FIPS Series under FIPS 140-3.
FIPS-specific Aspects of the YubiKey 5 FIPS Series
For a description of the FIPS-specific aspects of the YubiKey 5 FIPS Series with the 5.7.4 firmware, see YubiKey 5 FIPS Series under FIPS 140-3.
The table below lists the YubiKey 5 FIPS Series with the 5.4 firmware configuration changes that are set at programming. These are in addition to the configuration options available in the YubiKey 5 FIPS Series.
| Configuration Change | Description |
|---|---|
| Functional | Enforce power-up self-test (firmware integrity and
algorithm testing)
|
Minimum PIN length
for FIDO2
|
6 alphanumeric characters |
Identification
(FIDO)
|
Unique AAGUIDs for the FIDO Attestation
See AAGUID Values in FIPS AAGUID and Form Factors.
|
| Attestation (FIDO) | Attestation certificates for FIDO include
a FIPS OID (1.3.6.1.4.1.41482.12)
|
FIDO GETINFO |
Command returns a listing of FIPS certificates
applicable to the specific authenticator.
|
| Attestation (PIV) | Attestation certificates for PIV include
the FIPS Form Factor identifier** in the
Form Factor OID (1.3.6.1.4.1.41482.3.9)
|
| YubiKey Manager | Form factor identifies FIPS Series devices.
|
FIDO Authenticator Supported Certifications
The certifications that are supported by a FIDO authenticator can be returned in the certifications member of an authenticatorGetInfo response as set out in paragraph 7.3.1. Authenticator Actions of the Client to Authenticator Protocol (CTAP) Review Draft of March 09, 2021.
FIPS AAGUID and Form Factors
Form factor is set during manufacturing and returned as a one-byte value. Currently defined values for this are set out in the Form Factor table below:
Form Factor
|
YubiKey Value
|
Security Key
Value, FW 5.4+
|
FIPS YubiKey
Value, FW 5.4+
|
|---|---|---|---|
| UNDEFINED | 0x00 | N/A | N/A |
| Keychain, USB-A | 0x01 | 0x41 | 0x81 |
| Nano, USB-A | 0x02 | N/A | 0x82 |
| Keychain, USB-C | 0x03 | 0x43 | 0x83 |
| Nano, USB-C | 0x04 | N/A | 0x84 |
Keychain with
Lightning, USB-C
|
0x05 | N/A | x85 |
YubiKey 5 CCN Series
The YubiKey 5 CCN Series is a standard YubiKey 5 Series key running firmware version 5.7.4 that is certified by the National Cryptologic Centre (CCN). This certification enables Spanish public organizations to comply with Royal Decree/Real Decreto 311/2022.
The YubiKey 5 CCN Series has been added to the CPSTIC catalog, Catálogo de Productos y Servicios de Seguridad de las Tecnologías de la Información y la Comunicación (CPSTIC), Yubikey 5 CCN Serieis 5.7.4, in compliance with Guía de Seguridad de las TIC, CCN-STIC 105.
To meet the CCN requirements, deploy the YubiKey CCN Series in accordance with the following:
- CCN compliance is focused on strong cryptographic authentication methods, specifically FIDO2 and PIV. Other protocols are not covered by CCN requirements.
- FIDO2 - Use PINs to protect all discoverable credentials.
- PIV - Use either RSA 3072 bytes and above or ECC based private keys.
- PIV - Change PIN, PUK, and Management keys from default. Block PUK codes if they are not required.
See also Yubico Support:
YubiKey 5 Enhanced PIN Series
The YubiKey 5 Enhanced PIN Series provides a standard YubiKey 5 Series key with fixed settings for 6 character minimum PIN length, PIN complexity, and always on verification.
Based on the YubiKey 5 Series, the Enhanced PIN Series features include:
Uses the FIDO (FIDO2/FIDO U2F) protocol. See FIDO2.
Is available in USB-A + NFC and USB-C + NFC form factors. See YubiKey Enhanced PIN Series.
Ships with firmware version 5.7.4 or later. See Firmware Overview.
Has a serial number to enable asset tracking.
The serial number is on the back of the key and can also be read programmatically through the FIDO HID (Human Interface Device) interface.
Enables access to the serial number over CCID running firmware version 5.7.x. See CCID.
The serial number is retrievable by client software in Windows without requiring elevated privileges (admin rights) since the YubiKey management application is accessible via CCID, which enables use cases where client software needs to read the serial number of the authenticator.
Enforces PIN Complexity. This cannot be changed.
Increases in the minimum FIDO pin length to 6. See Minimum PIN Length and Minimum PIN Length Extension.
Enforces user verification always on, Always User Validation.
For a list of YubiKey 5 Enhanced PIN Series specifications, see the YubiKey 5 Series Product Brief.
For AAGUID, see YubiKey hardware FIDO2 AAGUIDs.
YubiKey Bio Series
The YubiKey Bio Series offers the familiar YubiKey experience users have come to know and trust, but adds the convenience of a new biometric touch feature. The following is a summary of the features; for complete explanations, see YubiKey Bio Series Specifics.
New York State’s Department of Financial Services (DFS) advises that instead of using a traditional fingerprint or other biometric authentication system, the services regulated by DFS should consider using an authentication factor that employs technology with liveness detection or texture analysis to verify that a print or other biometric factor comes from a live person. This is what the new biometric touch feature provides.
The series is comprised of four keys:
- The YubiKey Bio - FIDO Edition (USB-A form factor)
- The YubiKey C Bio - FIDO Edition (USB-C form factor)
- The YubiKey Bio - Multi-protocol Edition (USB-A form factor)
- The YubiKey C Bio - Multi-protocol Edition (USB-C form factor)
Up to five fingerprints can be stored on a YubiKey Bio.
For a list of YubiKey Bio Series specifications, see the YubiKey Bio Series Product Brief.
For AAGUIDs, see YubiKey hardware FIDO2 AAGUIDs.
YubiKey Bio Multi-protocol Edition
The YubiKey Bio Multi-protocol Edition is a new product that combines the ease of use of the YubiKey Bio FIDO Edition with a PIV-like smart card interface and unified PIN and fingerprint templates. This unique combination produces a portable authenticator with the convenience of biometric authentication and support for desktop login.
The YubiKey Bio Multi-protocol Edition takes a novel approach to PINs and fingerprints by using the same PIN and fingerprint templates for both FIDO and smart card. The resulting experience is seamless provisioning and use across both desktop sign-in and web use cases. This thereby eliminates the need for the user to enroll fingerprints multiple times or manage individual PINs.
Protocols Supported
FIDO Protocols
All keys in the YubiKey Bio Series support WebAuthn sites and applications that support the FIDO2 and FIDO U2F protocols. FIDO2 (sometimes referred to as WebAuthn) builds upon FIDO U2F, and is the standard that enables the replacement of password-based authentication. For more information, see YubiKey Bio and FIDO2 and YubiKey Bio and FIDO U2F.
Each application can be enabled and disabled independently. However, even though the firmware applications are separate from one another, they both share the same PIN and FIDO reset capability, which is to say that a FIDO reset resets both applications. To manage these applications, see Tools.
PIV Protocol
The YubiKey Bio Multi-protocol Edition also supports the PIV protocol, and works with sites and applications that support PIV/smart card interfaces. In order to use the biometric feature on the YubiKey Bio Multi-protocol Edition, the YubiKey Minidriver (Windows) is required (the Minidriver download is the third item on the page). See YubiKey Minidriver User Guide.
Using the YubiKey Bio
For a quick start to using the YubiKey Bio Series, without a lot of details, see Yubico’s setup page.
This guide, the YubiKey Technical Manual, provides:
- How the YubiKey Bio Works)
- Descriptions of the different User Experiences with the various protocols
- Full instructions for enrolling fingerprints using platform support:
- Descriptions of the methods by which the protocols are supported, in:
- A brief explanation of the role the Yubico Authenticator plays in managing the YubiKey Bio.
Usage Notes
The YubiKey Bio implements biometrics as outlined in the CTAP 2.1 specification. The best user experiences are provided by the YubiKey Bio with client applications and browsers that also implement CTAP 2.1. Applications and browsers that implement CTAP 1 or CTAP 2.0 also work with the YubiKey Bio. However, the UI on client devices is not as intuitive and there might be some limitations.
Interfaces
Like all YubiKeys, the YubiKey Bio Series are USB 2.0 devices.
Note
Developers: The USB PID and iProduct string are 0x0402 and YubiKey FIDO respectively. See YubiKey USB ID Values.
Security Key Series
The Security Key Series are only available with the FIDO (FIDO2/FIDO U2F) protocol and is only available in USB-A + NFC and USB-C + NFC form factors. The lastest FIDO updates are included with the latest YubiKey firmware on all Sercurity Key Series.
The Security Key Series - Enterprise Edition includes the features of the Security Key Series and has the following additional updates:
A serial number to enable asset tracking. The serial number is on the back of the key and can also be read programmatically through the FIDO HID interface.
Access the serial number over CCID for Security Key - Enterprise Edition running firmware version 5.7.x. See CCID.
The serial number is retrievable by client software in Windows without requiring elevated privileges (admin rights) since the YubiKey management application is accessible via CCID, which enables use cases where client software needs to read the serial number of the authenticator. This change was introduced in 5.7.0.
PIN Complexity turned on by default (and cannot be turned off).
Increase in minimum FIDO pin length to 6. See Minimum PIN Length and Minimum PIN Length Extension.
Capability
|
5.7.x
Enterprise Edition
|
5.7.x
|
5.4.x
Enterprise Edition
|
5.0.x-5.4.x
|
|---|---|---|---|---|
| Serial Number | Yes | No | Yes | No |
| Serial Number over CCID | Yes | No | No | No |
| PIN Complexity | Yes | No | No | No |
| FIDO Minimum PIN Length | 6 | 4 | 4 | 4 |
For a list of Yubico Security Key Series specifications, see the Security Key Series Product Brief.
For AAGUIDs, see YubiKey hardware FIDO2 AAGUIDs.
YubiKey 5 CSPN Series
Important
The YubiKey 5 CSPN Series has been discontinued.
Instructions on how to configure and use the YubiKey 5 in compliance with CSPN (“Certificat de Sécurité de Premier Niveau” [RD1]) are given in YubiKey 5 CSPN Series Specifics.
For each YubiKey application that requires specific configuration, there is a short introduction, the required settings to achieve the target, and a technical description of the configuration.
Firmware
For a summary overview of the firmware features, see Firmware Overview, which includes the capability matrices, listing the features and form factors available per firmware version for each of the products in the YubiKey 5 Series and the Security Key Series.
For more in-depth information about:
- the most recent firmware release, see 5.7.4 Firmware
- the firmware between 5.6 and 5.7.4, see 5.6 and 5.7 Firmware Prior to 5.7.4
- the firmware prior to 5.6, see Firmware Specifics Prior to 5.6.x
Note
Yubico periodically updates its firmware to take advantage of features and capabilities introduced into the ecosystem. YubiKeys are programmed in Yubico’s facilities with the latest available firmware. Once programmed, YubiKeys cannot be updated to another version. The firmware cannot be altered or removed from a YubiKey.
The firmware version on a YubiKey or a Security Key determines whether or not a feature or a capability is available to that device. The quickest and most convenient way to determine your device’s firmware version is to use either the Yubico Authenticator with its intuitive and easy-to-use (GUI) interface or ykman the lightweight command line (CLI) software package installable on many OSs.
NIST: FIPS
Yubico submitted the firmware for releases 5.4.2 and 5.4.3 to NIST and the organization approved the certification. The certificates can be found here. For more information about the YubiKey 5 FIPS Series, see YubiKey 5 FIPS Series Specifics.
CCN: 5 Series NFC
Yubico submitted the firmware for release 5.7.4 to the Certification Organization for the National Cryptologic Centre (CCN) and the organization approved the certification. The CCN Certification is published in the CPSTIC catalog, Catálogo de Productos y Servicios de Seguridad de las Tecnologías de la Información y la Comunicación (CPSTIC), Yubikey 5 CCN Serieis 5.7.4.
For more information about the YubiKey 5 CCN Series, see YubiKey 5 CCN Series.
ANSI: CSPN
The YubiKey 5 CSPN Series has been discontinued.
Yubico submitted release 5.4.2 to ANSSI for certification and the organization approved the certification. For more information about the YubiKey 5 CSPN Series, see YubiKey 5 CSPN Series.