YubiEnroll with Microsoft Entra ID
The following describes how to set up YubiEnroll in the Microsoft Entra ID tenant and configure the required user permissions.
Configuration Steps
The configuration steps involve the following:
- Enabling multi-factor authentication for YubiKeys in Microsoft Entra ID.
- Registering the YubiEnroll application in Microsoft Entra ID.
- Configuring the YubiEnroll permissions in Microsoft Entra ID.
- Adding the Microsoft Entra ID provider in YubiEnroll.
When you have successfully completed these steps, you are ready to enroll YubiKeys on behalf of end users in your organization.
Enabling MFA for YubiKeys
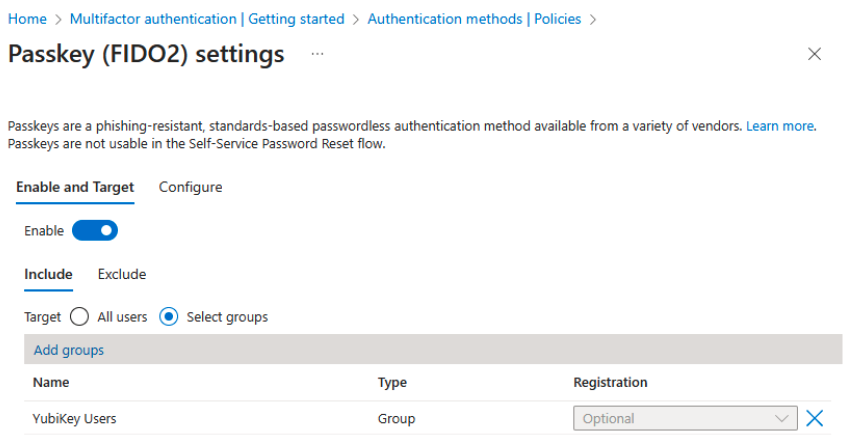
Ensure that Microsoft Entra ID Multi-Factor authentication (MFA) for Passkey (FIDO2) is enabled and that the target user accounts for YubiEnroll enrollment are in the scope.
To enable MFA for target user accounts, log in to the Entra admin center and go to Identity > Protection > Authentication methods > Policies > Passkey (FIDO2).
Enable the feature and either select all users, or select groups to be in the scope for YubiEnroll enrollment. For more information on configuring FIDO authentication with YubiKeys in Entra ID, see Enable passkeys (FIDO2) for your organization (Microsoft documentation).
Registering the YubiEnroll App
When configuring the Microsoft Entra ID provider in YubiEnroll, the following parameter values are needed:
client_idtenant_idredirect_uri
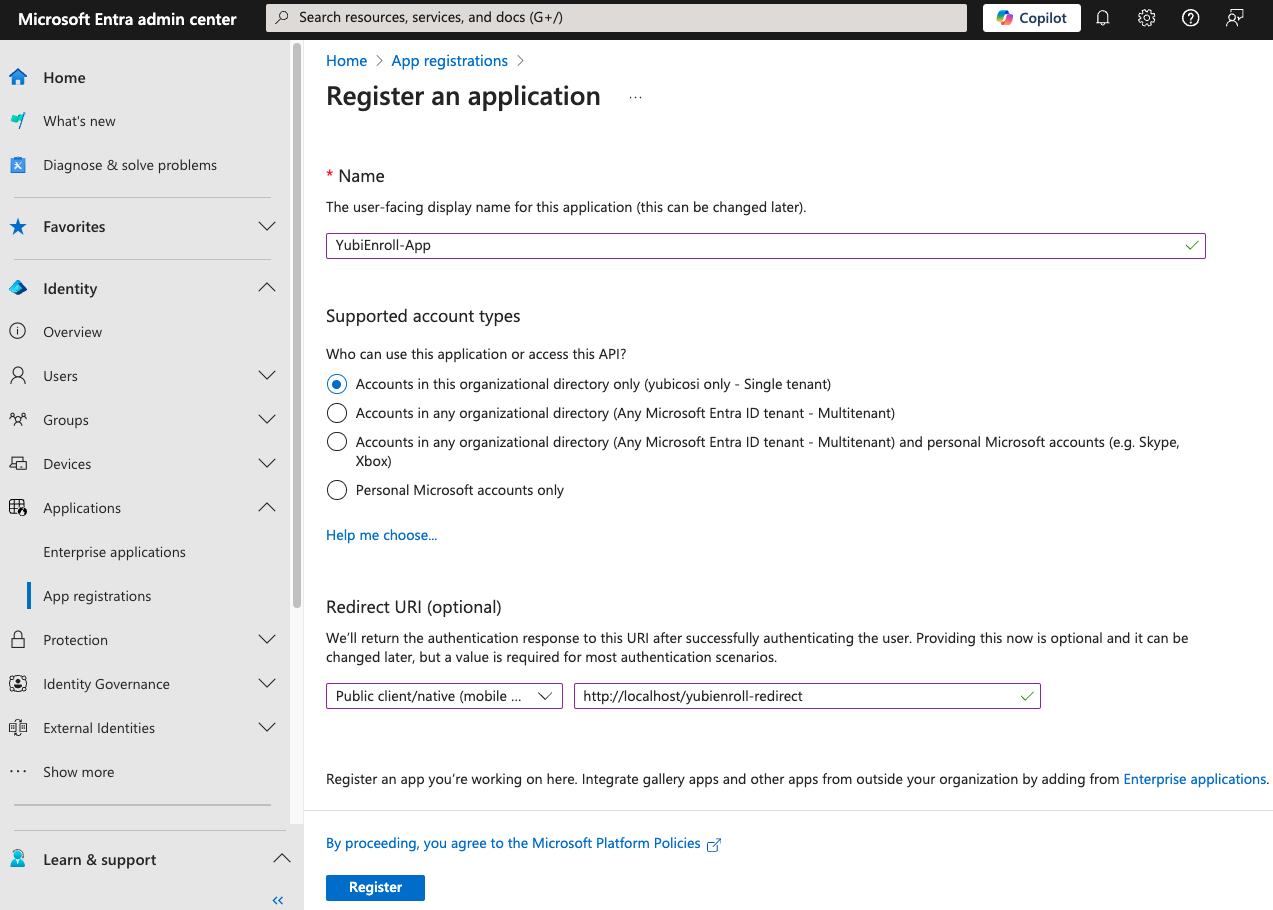
These parameter values are created when registering the YubiEnroll (OAuth) application in Microsoft Entra ID. To register the YubiEnroll app, log in to the Entra admin center, go to Application > App registrations and select New registration.
When registering the YubiEnroll app, ensure the following:
Select Public client/native (mobile & desktop) as the platform type.
The Redirect URI must start with “http://localhost”, for example “http://localhost/yubienroll-redirect”. You do not need to specify the port as Microsoft Entra ID supports ephemeral ports.
For more details on how to register the YubiEnroll app, see Register an application with the Microsoft identity platform (Microsoft documentation).
Configuring Permissions
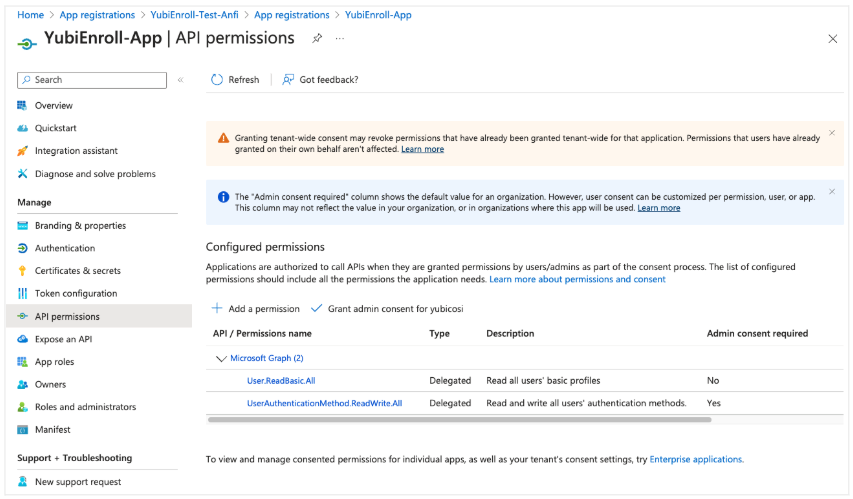
The YubiEnroll app requires the following two permissions in Microsoft Entra ID to be added as Microsoft Graph Delegated permissions:
- User.ReadBasic.All
- UserAuthMethod.ReadWrite.All
To add these, open the YubiEnroll app in Microsoft Entra ID, select API permissions in the left menu, and click Add a permission.
Note
When registering an app in Microsoft Entra ID, two types of Microsoft Graph permissions can be assigned: Application and Delegated. For YubiEnroll it is crucial to only configure Delegated permissions to ensure that the app’s access is limited to the logged in user’s permissions.
When combined with the Microsoft Entra ID feature “Administrative units”, this setup allows for fine-grained control of access based on groups, users, or specific properties such as location. An example where this can be leveraged is where an administrator could be allowed to manage YubiKey enrollments only for users in their administrative unit. To review permissions granted to a registered app, check the Type settings under API permissions for the app.
For a user to be able to grant consent to these permissions when setting up the application in Microsoft Entra ID, the user must be assigned the Global Administrator role.
For more information about app permissions, see Overview of Microsoft Graph permission (Microsoft documentation).
The following applies when configuring permissions:
- Authentication Administrator role is required for managing passkeys of non-administrators.
- Privileged Authentication Administrator role is required for managing passkeys for any type of user including Global Administrators.
Important
Even with the Privileged Authentication Administrator, an administrator will not be able to use YubiEnroll to manage passkeys for their own profile.
For more information, see Authentication Administrator (Microsoft documentation) and Privileged Authentication Administrator (Microsoft documentation).
Adding the Entra ID Provider
Before you can run YubiEnroll with Microsoft Entra ID, you must add the provider configuration in YubiEnroll.
When adding a provider configuration in YubiEnroll you will need the following values, created when the app was registered.
- Application (client) ID
- Directory (tenant) ID
- Redirect URI
To find these values in Microsoft Entra ID, locate the YubiEnroll app and select Overview. The values are displayed in the Essentials section for the app.
For information on how to add a provider configuration in YubiEnroll, see Adding Provider Configurations and YubiEnroll Commands.
Note
When configuring a Microsoft Entra ID provider, you will be prompted to specify the Microsoft Entra ID endpoint which defaults to “https://login.microsoftonline.com”, and the Microsoft Graph endpoint which defaults to “https://graph.microsoft.com”. The normal case is to use these default values. However, if you are using national cloud deployments you will need to change these endpoints. For more information, see Microsoft Graph national cloud deployments (Microsoft documentation).