YubiKey Bio Series Specifics
Additional Physical Attributes
Laser Marking
The laser marking of the FIDO Edition of the YubiKey Bio Series was changed in March 2024. To distinguish the FIDO Edition from the Multi-protocol Edition, ‘FIDO’ is marked on the back near the serial number and data matrix. YubiKeys of product type YubiKey Bio Series - FIDO Edition produced before March 2024 do not have ‘FIDO’ marked on the back, instead they have only the serial number and data matrix on the back.

YubiKey Bio Series - FIDO Edition marked ‘FIDO’, March 2024 and later

YubiKey Bio Series - Multi-protocol Edition and YubiKey Bio Series - FIDO Edition prior to March 2024
Sensors
The YubiKey Bio recognizes two interactions, one a touch, and the other a fingerprint. Its recognition of the fingerprint - or lack thereof - is communicated through the LEDs. See LED Behavior.
On the YubiKey Bio, the silver-colored bezel encircling the fingerprint sensor provides the grounding plane required to read the fingerprint. Touch types:
| Biometric: | When prompted to have the YubiKey Bio read your fingerprint from the fingerprint sensor, be sure to touch at least a tiny part of the ring. If you use your little finger to touch only the center of the fingerprint sensor, the key does not read the fingerprint. |
|---|---|
| Plain: | When prompted to touch the YubiKey Bio but not explicitly asked for the fingerprint, touch both the bezel and the fingerprint sensor, even though the fingerprint is not read. |
Fingerprint Tips provides detailed instructions on using the fingerprint sensor.
LEDs
The YubiKey Bio has a green LED and an amber LED to provide direct feedback. It flashes when the key is ready for interaction or is communicating something about the interaction. LED Behavior provides detailed descriptions.
Ratings
The YubiKey Bio has been IP68-rated under the IEC standard 60529.
Care and Cleaning
To clean the YubiKey and sensor, use only wipes impregnated with no more than 70% isopropyl alcohol.
Requirements: Platform and Browser Compatibility
Desktop
The YubiKey Bio Series works with the latest versions of most browsers and desktop operating systems. Currently, the best experience can be had on macOS, Chrome OS, and Linux, running up-to-date Chromium-based browsers.
On Windows 10, browsers are not currently able to tell you when the YubiKey has failed to match the fingerprint, so you must watch for the YubiKey’s blinking amber LED to indicate if an attempt has failed. Windows 11 does not have this problem.
On other platforms, browsers such as Firefox and Safari have not yet (at the time of writing) implemented CTAP 2.1 and therefore you are typically prompted to enter the PIN even if the key is not in the “biometrics blocked” state.
Mobile
- The YubiKey Bio does not have NFC capabilities.
- The YubiKey Bio can be used with mobile, but it is reliant on mobile operating system support as well as on browser support for the FIDO protocols. For more information, please refer to the relevant manufacturer’s web sites for your mobile device.
- When the YubiKey Bio has fallen back to requiring the PIN, you might need to resort to a computer (as opposed to a mobile device) to unblock biometrics (see: Unblocking and Resetting the YubiKey Bio).
YubiKey Bio and FIDO2
The YubiKey Bio Series - FIDO Edition and the Multi-protocol Edition support all FIDO2 scenarios supported by the YubiKey 5 Series and the Security Key Series. They can be used in both passwordless and second factor authentication scenarios. In both scenarios the fingerprint is used in lieu of the PIN, the way biometrics are used on a smartphone. There are some scenarios in which the PIN is required; for example, when enrolling or otherwise managing fingerprints, just as it is on a smartphone. The only opportunity to input the PIN is after 3 unsuccessful attempts at matching a fingerprint with an enrolled fingerprint.
Fingerprint Authentication
When biometrics is not blocked on the YubiKey Bio, the user has three opportunities to present a valid fingerprint by touching the fingerprint sensor. The platform - for example, the browser or desktop client - will notify the user if the fingerprint was recognized, i.e., the attempt was successful. If unsuccessful, the YubiKey Bio’s amber LED will also blink 3 times.
After three unsuccessful fingerprint attempts the platform will prompt for PIN entry. For more information on the FIDO2 PIN see FIDO2 PIN.
Discoverable Credentials
Like FIDO U2F, the FIDO2 standard offers the same high level of security, as it is based on public key cryptography. In addition to providing phishing-resistant two-factor authentication, the FIDO2 application on the YubiKey allows for the storage of discoverable credentials. (Fingerprint templates are not discoverable credentials.) Keys in the YubiKey Bio Series can hold up to 25 discoverable credentials (firmware 5.5 and 5.6) or 100 discoverable credentials (firmware 5.7 and later). To manage them, see Credential Management.
FIDO2 Credentials
The discoverable credentials can be used for passwordless authentication, or they can be used for two-factor authentication. In both scenarios the credentials can be protected by the FIDO2 PIN and in the case of a YubiKey Bio, biometrics can be used in lieu of the PIN provided that fingerprints have been enrolled and that the key is not in biometrics blocked state.
Credential Management
If you decide to discontinue using a site or service, you can delete its discoverable credential. This frees up space on the YubiKey Bio, which can contain up to 25 discoverable credentials (firmware 5.5 and 5.6) or 100 discoverable credentials (firmware 5.7 and later).
To view the discoverable credentials on your YubiKey and delete them selectively, use the Yubico Authenticator for Desktop version 5.1.0 and above.
For more information on credentials in general, and in particular on managing them, see Enhancements to FIDO 2 Support.
For more developer-oriented information on this, see Discoverable Credentials / Resident Keys on Yubico’s developer site.
FIDO2 PIN
The FIDO2 PIN is necessary for:
- Enrolling fingerprints
- Managing enrolled fingerprints
- Fallback after failure to match fingerprint with template.
- There is no PIN set by default
- Once a FIDO2 PIN is set, it can be changed but it cannot be removed unless you reset the FIDO2 application.
- If the FIDO2 PIN is entered incorrectly three times in a row, the key needs to be reinserted before it can accept additional PIN entry attempts. Reinserting “reboots” the key.
- To find out how many retries you have left, use the Yubico Authenticator tool or the ykman tool.
- If the PIN is entered incorrectly eight times in a row (3+3+2), the FIDO2 application locks, and FIDO2 authentication is not possible.
- To restore the FIDO2 functionality, reset the FIDO2 application.
For YubiKey Bio Series - FIDO Edition keys, the FIDO2 PIN must be between 4 and 63 characters in length. For YubiKey Bio Series - Multi-protocol Edition keys, PIN length requirements depend on firmware version and YubiKey application status:
YubiKey Bio Series - Multi-protocol Edition
PIN Length Requirements
|
||
|---|---|---|
| Firmware version: | PIV application enabled: | PIV application disabled: |
| Prior to 5.7.4 | 6-8 characters | 4-63 characters |
| 5.7.4 and later | 6-8 characters | 6-63 characters |
For more information, see Understanding YubiKey PINS and Device PIN.
Note
Resetting the FIDO2 application also resets the U2F application. No site you have registered the YubiKey with using U2F will work until the YubiKey is re-registered with that site.
User Verification
The YubiKey Bio implements always-on user verification, or alwaysUV.
The user verification requirement asks for proof that the user logging in is the same user as the one who set the PIN, enrolled fingerprints, and registered the key with the app or service (Relying Party, or RP). For more information about user verification, see User Presence vs User Verification.
When userVerification is discouraged, the user experience is not optimal unless the platform has implemented CTAP 2.1. See Multifactor Authentication (MFA).
Supported Extensions
The YubiKey Bio supports the AppID extension (appid) as defined by the W3C Web Authentication API specification. This extension allows U2F credentials registered using the legacy FIDO JavaScript APIs to be used with WebAuthn. In practice, that means that if you register a YubiKey Bio on a website when it used U2F and that website later upgrades to FIDO2, previously registered U2F credentials continue to work.
Note
Developers: For AAGUID values, see YubiKey Hardware FIDO2 AAGUIDs.
YubiKey Bio and FIDO U2F
The FIDO U2F protocol does not require any special drivers or configuration to use, just a compatible web browser. The U2F application on the YubiKey can be associated with an unlimited number of WebAuthn sites supporting FIDO U2F authentication.
FIDO U2F on the YubiKey Bio Series requires that the touch be a successful biometric match with an already enrolled fingerprint. This is different from FIDO U2F on other YubiKeys.
PIN + U2F
As the concept of PIN does not exist in FIDO U2F, after three successive failures to match the fingerprint, the key goes into the “biometrics blocked” state without first prompting for the PIN. An amber LED blinks slowly and continuously to indicate this state. Biometrics can be unblocked with a FIDO2 operation using the PIN (that is, authentication). See Troubleshooting and Tools for full instructions and more information.
Note
Developers: With regard to computer login tools that use FIDO U2F for second-factor authentication, some software might use a YubiKey and FIDO U2F as a second factor. Since FIDO U2F has no concept of fallback to PIN, the YubiKey Bio is not likely to be a good choice for this use case. For more information about software that falls into this category, visit Yubico’s Support site and look for articles about the YubiKey Bio: https://support.yubico.com/hc/en-us/search?query=YubiKey+Bio
FIDO U2F Succeeded by FIDO2
FIDO2 is the umbrella term used to describe an amalgamation of two separate sets of specifications: WebAuthn and the Client-to-Authenticator Protocol, CTAP (currently version 2.1, and often referred to as CTAP2.1). The WebAuthn component provides a narrow scope of flexibility for developers on the service layer because it encompasses the logical interactions across a network. CTAP2.1, however, provides a much more open set of standards for the interaction between a security device and the user.
CTAP2.1 is also where biometrics such as fingerprint enrollment, management, and use were first defined. To create a cohesive user experience, adherence to this specification is required from:
- Authenticators such as the YubiKey Bio
- Clients such as the Chrome or Edge browsers
- Platforms such as Windows and macOS.
See User Experiences.
Supported Extensions
The YubiKey Bio supports the AppID extension (appid) as defined by the W3C Web Authentication API specification. This extension allows U2F credentials registered using the legacy FIDO JavaScript APIs to be used with WebAuthn. In practice, that means that if you register a YubiKey Bio on a website when it used U2F and that website later upgrades to FIDO2, previously registered U2F credentials continue to work.
Note
Developers: For AAGUID values, see YubiKey Hardware FIDO2 AAGUIDs.
YubiKey Bio and PIV
The YubiKey Bio Multi-protocol Edition supports PIV in addition to FIDO U2F and FIDO2. The PIV application works the same way as the PIV application on a YubiKey 5 Series, see Smart Card (PIV Compatible), with the differences set out below.
Device PIN
On the YubiKey Bio Multi-protocol Edition, the PIN is shared between the PIV and FIDO2 applets. PIN length requirements depend on firmware version and YubiKey application status.
How the YubiKey Bio Works
For the full technical explanation of this from a developer perspective over FIDO, start with the Yubico’s WebAuthn Developer Guide.
Note
In the following, the term credentials is referenced repeatedly. There are different kinds of credentials. To pursue all the distinctions, consult the FIDO2 page on the Fido Alliance web site.
Enrollment
Before you can start using the YubiKey Bio with services and applications, you need to first set a FIDO2 PIN. Once a PIN is set, biometric functionality (recommended but not required for use with passkeys) can be enabled by enrolling at least one fingerprint. The YubiKey Bio needs to have the PIN as a fallback in case it cannot recognize your fingerprint.
Although there are two FIDO applications on the YubiKey Bio, namely FIDO2 and U2F, it is the FIDO2 PIN that is required as fallback for both. The PIN is not associated with any site. When the fingerprint does not work and the key falls back to the PIN, it is the key that needs the PIN for authentication to all sites, including U2F sites (even though U2F has no concept of PIN). With fallback to PIN, it is easy if you are authenticating to a WebAuthn/FIDO2 site, because the browser/client app can prompt for the PIN. Otherwise you must unblock biometrics by using any of the following:
- The YubiKey Bio start page
- The Yubico Authenticator
- The ykman Releases page.
The “working” of the fingerprint is described in the following. For information on how and why the fingerprint might not “work”, see Fingerprint Tips.
Risk Mitigation
To mitigate the risk of being shut out of your account or service, it is always advised to register a second YubiKey. For more information, see https://www.yubico.com/spare/.
Fingerprints and Templates
An enrolled fingerprint is stored on the YubiKey Bio not as an image, but in the form of a template, similar to a one-way hash. It is not possible to recreate an image of a fingerprint from a template, nor does the template ever leave the YubiKey.
After enrollment, each time you apply your fingertip to the fingerprint sensor, the key tries to match the fingerprint against the template stored on the key.
Parties Involved in Registration and Authentication
Closely related to Requirements: Platform and Browser Compatibility, registering and authenticating with a YubiKey Bio to an app or a service that supports WebAuthn or U2F involves several parties:
- The user (with their fingerprints and knowledge of the PIN)
- The YubiKey Bio
- The FIDO2 application or the U2F application on the YubiKey Bio
- The FIDO2/WebAuthn or U2F-supporting browser or client
- The service or app
All these work together. For example, if your YubiKey does not work as expected, you might be using a browser or an app that does not support FIDO2 security keys.
- YubiKey Bio Multi-protocol Edition
- When using the YubiKey Bio Multi-protocol Edition the client needs to support the PIV protocol and the client needs to have the Yubico Minidriver installed (version 4.6.0 or later).
Registration
Registering a YubiKey Bio with a site, service, or application is the same as for other YubiKeys.
Authentication
Depending on the protocol supported by the site or service, there are several possible user experiences (scenarios). These are described below.
User Experiences
The user experience with the YubiKey Bio is dictated by a combination of the site or service that the user is authenticating against and the browser or client. Different service and client combinations yield different results. The user experiences are determined by the different options for developers implementing FIDO2 with the WebAuthn and CTAP protocols. Please note that the following descriptions of user scenarios are only high-level overviews. The experiences change every time the various forms of support change.
Passwordless
This scenario provides the best user experience by enabling a passwordless flow backed by strong authentication. To achieve it, use discoverable credentials. When the user authenticates to the site or service:
- The client or browser prompts the user to insert the YubiKey.
- The client makes a request to the YubiKey to see if any credentials on the key have been registered for use with this site or service.
- If the correct credentials are found, the client or browser prompts the user to apply their fingertip to the YubiKey Bio’s sensor.
- If the fingerprint match is successful, the appropriate response is sent to the client or browser to complete authentication.
- If the fingerprint match is unsuccessful three times in a row, the client or the browser prompts instead for the PIN. After correctly inputting the PIN, the user is then prompted to touch the key to prove presence (as opposed to verifying identity). In this situation, the YubiKey Bio behaves like any other key in the YubiKey 5 Series.
Multifactor Authentication (MFA)
When a user authenticates to the site or service,
- The client or browser prompts the user to insert their username and password. These are what the server uses to identify the user and determine whether they are registered.
- If username and password match the server’s records, the site or service prompts the user for an additional form of identification to prove their identity. This is called multifactor authentication.
- The user proves their identity to the key either by providing a fingerprint that the key can match to its template, or by entering the PIN.
- If the fingerprint match is successful, the appropriate response is sent to the client or browser to complete authentication.
- If the key is unsuccessful at matching fingerprint to template three times in a row, the YubiKey Bio goes into the biometrics blocked state, signaling this by slow constant flashing of the amber LED. The client or the browser prompts instead for the PIN and for the user to touch the key (checking for user presence). In this situation, the YubiKey Bio behaves like any other key in the YubiKey 5 Series.
U2F
This scenario only works well if the fingerprint match is successful and the user flow is the same as the multifactor flow. If the fingerprint match is unsuccessful, any prompts from the site or service are unlikely to be clear and unambiguous, because U2F has no concept of PIN.
If the fingerprint match is unsuccessful, you must unblock biometrics by using any of the following:
- The YubiKey Bio start page
- The Yubico Authenticator tool
- The ykman tool.
Unblocking and Resetting the YubiKey Bio
The main cause for the biometric function to block is failure to match the fingerprint three times in a row. If the YubiKey Bio locks because the biometric function was blocked, you can just unblock it instead of resetting it: see Troubleshooting and Tools.
Locking/Blocking
| Fingerprint: | If the YubiKey cannot match fingerprint to template three times in a row, fingerprint recognition is blocked. The YubiKey Bio falls back to PIN. |
|---|---|
| PIN: | If you enter the wrong PIN eight times in a row, the YubiKey FIDO2 application becomes locked, which means it cannot communicate with you or with any site or service. It indicates the blocked state by flashing its amber LED slowly and continuously. In order to restore this functionality, reset the FIDO2 application. For more details, see FIDO2 PIN. |
| Unblock: | To unblock the YubiKey Bio’s biometric function (its ability to read fingerprints) by using any of the following:
|
Resetting
Resetting your YubiKey Bio deletes all credentials, the PIN, and stored fingerprint templates.
Resetting the key is not the same as unblocking it. Resetting the FIDO2 and FIDO U2F applications returns the key to the factory default state. In this default state, the key has neither fingerprints nor PIN nor credentials. After resetting it, you must therefore enroll your fingerprints again and register your key again to your apps and services. See the relevant Enrolling chapter, either Using Chrome to Enroll Fingerprints or Using Windows to Enroll Fingerprints.
Note
The YubiKey Bio Multi-protocol Edition behaves differently from other YubiKey Bios. To ensure that devices and applications do not unintentionally destroy credentials on that key, if both PIV and FIDO are enabled, the native reset commands for these protocols will be disabled and replaced with a single new reset command for both applications.
Therefore, if you try to run the individual protocol resets on a YubiKey Bio Multi-protocol Edition, you will get an error message. Conversely, if you try to run the reset command for the YubiKey Bio Multi-protocol Edition on a YubiKey Bio that is not the Multi-protocol Edition, you will also get an error message.
Because the PIN and fingerprint templates have been unified, the individual PIV and FIDO2 protocols can only be enabled or disabled on a freshly reset device. It is not possible to enable or disable protocols after a PIN is set.
Resetting Your YubiKey Bio with the Yubico Authenticator and Other Tools
With a YubiKey Bio that is not the Multi-protocol Edition, resetting means resetting the FIDO application. You can perform a FIDO reset using any of the following:
- The YubiKey Bio start page
- The Yubico Authenticator tool
- The ykman tool
- Windows Sign-in options
- The Chrome browser settings.
YubiKey Bio Multi-protocol Edition
To reset the YubiKey Bio Multi-protocol Edition please use the Yubico Authenticator tool.
Managing Credentials
If you decide to discontinue using a site or service, you can delete its discoverable credential. This frees up space on the YubiKey Bio, which can contain up to 25 discoverable credentials (firmware 5.5 and 5.6) or 100 discoverable credentials (firmware 5.7 and later).
To view the discoverable credentials on your YubiKey and delete them selectively, use the Yubico Authenticator for Desktop version 5.1.0 and above.
For more information on credentials in general, and in particular on managing them, see Enhancements to FIDO 2 Support.
For more developer-oriented information on this, see Discoverable Credentials / Resident Keys on Yubico’s developer site.
Using Chrome to Enroll Fingerprints
Set a PIN and enroll the first fingerprint using the Chrome browser on a macOS, Linux or Chrome OS device. To enroll more fingerprints use the Chrome settings as described in Enrolling Additional Fingerprints.
Note
A YubiKey is a FIDO2 hardware authenticator. Both Windows and Mac have built-in FIDO2 authenticators - that is, software authenticators that in this case are also platform authenticators. The prompts in both Windows and Mac might assume you are using their own authenticators. Therefore it is quite easy to register their authenticators with a site or service by mistake, without realizing that you are not registering your YubiKey. Read the prompts carefully to avoid this. And remember that the PIN is associated with the authenticator, not the site or service.
Although there are two FIDO applications on the YubiKey Bio, namely FIDO2 and U2F, it is the FIDO2 PIN that is required as fallback for both. The PIN is not associated with any site. When the fingerprint does not work and the key falls back to the PIN, it is the key that needs the PIN for authentication to all sites, including U2F sites (even though U2F has no concept of PIN). With fallback to PIN, it is easy if you are authenticating to a WebAuthn/FIDO2 site, because the browser/client app can prompt for the PIN. Otherwise you must unblock biometrics by using any of the following:
- The YubiKey Bio start page
- The Yubico Authenticator
- The ykman Releases page.
For information on the YubiKey Bio’s sensor and tips on working with fingerprints see Fingerprint Tips. For detailed information on FIDO2 PINs and their requirements, see Understanding YubiKey PINs.
Enrolling the First Fingerprint
| Step 1: | Use an up-to-date Chrome browser to open the YubiKey Bio Series setup website. Insert your YubiKey Bio into your computer. |
|---|---|
| Step 2: | Scroll down to the green button, Enroll using Chrome, and click it. The Use your security key with Yubico.com popup appears, this wizard walk you through the PIN setup (if no PIN is set) and fingerprint enrollment: 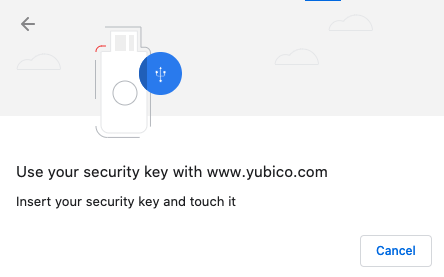
|
| Step 3: | If the amber LED flashes slowly, it means either no fingerprint is enrolled or biometrics is blocked. If you have reason to believe biometrics are blocked, go to the appropriate link on the YubiKey Bio Series setup page or to Troubleshooting and Tools. Otherwise, touch the key: 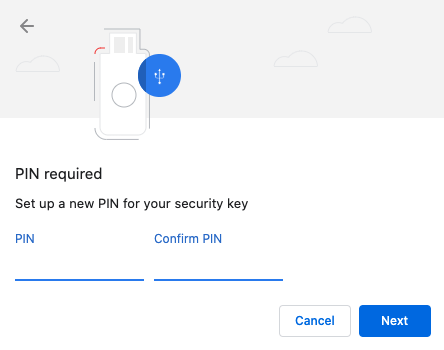
|
| Step 4: | If no PIN is set, set one by entering at least 4 digits, then confirm this PIN by re-entering it. If the YubiKey Bio already has a PIN set you are prompted to enter it. |
| Step 5: | When prompted, touch the fingerprint sensor and the bezel. You are prompted to touch the sensor several times, as set out below. Change the angle of finger to sensor slightly each time. Continue lifting and re-applying the same finger until the gray circle is entirely blue, the fingerprint icon is replaced by a tick mark, and the message in the popup reads “Your fingerprint was captured.” 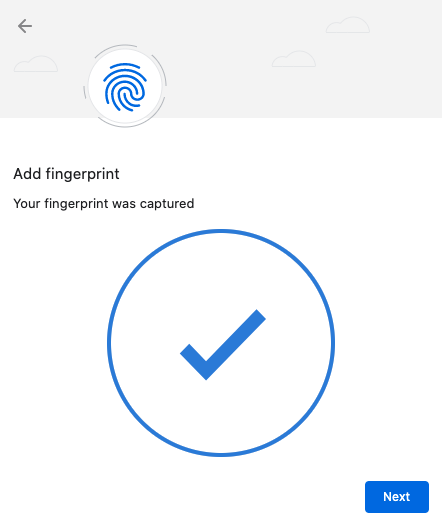
|
| Step 7: | Click Next. The Touch your security key again to complete the request popup appears: 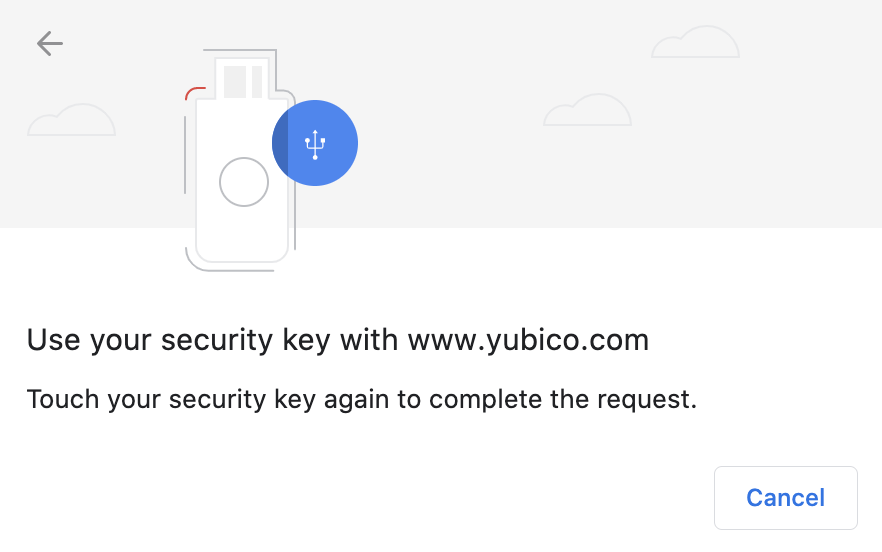
|
| Step 8: | Touch the bezel and sensor one last time. The final popup announces that enrollment was successful. The YubiKey Bio now has a template for that fingerprint. |
Enrolling Additional Fingerprints
If the YubiKey Bio already has fingerprint(s) enrolled on it, repeating the procedure for the first fingerprint does not work for subsequent fingerprints. Instead follow these steps.
Note
You can also use this method for setting a PIN for a new YubiKey Bio and enrolling all fingerprints.
| Step 1: | Either paste chrome://settings/securityKeys into the Chrome address field or click on the three vertical dots to the right of the URL field and navigate to Settings->Security->Advanced->Manage security keys. |
|---|---|
| Step 2: | Click Fingerprints and follow the instructions in the popup. |
Using Windows to Enroll Fingerprints
These are the instructions for setting a PIN on a YubiKey Bio and enrolling fingerprints on it using the Sign-in options on a Windows 10 or Windows 11 system.
Note
A YubiKey is a FIDO2 hardware authenticator. Both Windows and Mac have built-in FIDO2 authenticators - that is, software authenticators that in this case are also platform authenticators. The prompts in both Windows and Mac might assume you are using their own authenticators. Therefore it is quite easy to register their authenticators with a site or service by mistake, without realizing that you are not registering your YubiKey. Read the prompts carefully to avoid this. And remember that the PIN is associated with the authenticator, not the site or service.
Note
To get to the popup (prompt) for the YubiKey, you might need to cancel out of the pop-up for the built-in authenticator.
Although there are two FIDO applications on the YubiKey Bio, namely FIDO2 and U2F, it is the FIDO2 PIN that is required as fallback for both. The PIN is not associated with any site. When the fingerprint does not work and the key falls back to the PIN, it is the key that needs the PIN for authentication to all sites, including U2F sites (even though U2F has no concept of PIN). With fallback to PIN, it is easy if you are authenticating to a WebAuthn/FIDO2 site, because the browser/client app can prompt for the PIN. Otherwise you must unblock biometrics by using any of the following:
- The YubiKey Bio start page
- The Yubico Authenticator
- The ykman Releases page.
For information on the YubiKey Bio’s sensor and tips on working with fingerprints see Fingerprint Tips. For detailed information on FIDO2 PINs and their requirements, see Understanding YubiKey PINs.
| Step 1: | On Windows 10, click Enroll using Windows on the YubiKey Bio setup page <https://www.yubico.com/setup/yubikey-bio-series/>`_. On Windows 11, click Enroll using Windows on the YubiKey Bio setup page <https://www.yubico.com/setup/yubikey-bio-series/>`_. Then go to Step 3 below. |
|---|---|
| Step 2: | On Windows 10, in the expanded Security Key field, click Manage. 
|
| Step 3: | On both Windows 10 and Windows 11, follow the Windows setup directions. Insert the YubiKey Bio into your computer’s USB port and set a PIN for your YubiKey Bio if the key does not already have a PIN. In the Security Key PIN field, click Add. Enter a security key PIN and click OK. |
| Step 4: | To enroll your fingerprint, in the Security Key Fingerprint field, click Set up and follow the prompts. Touch the YubiKey Bio sensor while the green LED is still flashing, making sure to touch the ring-bezel as well. Vary the way you touch each time to include more of the fingerprint. If the fingerprint you enroll is smaller than the sensor, apply some pressure to help ensure a good image capture. Continue lifting and re-applying the same finger until you see the All set! message. Perform this step up to five times for a total number of 5 enrolled fingerprints. |
Fingerprint Tips
LED Behavior
The YubiKey Bio is not in a permanent state of readiness. It is therefore essential to wait for the key to signal its readiness by flashing the green LED before you touch it.
- If the key reacts to your touch by flashing or blinking the green LED, you used the right touch.
- If the amber LED flashes three times in quick succession, the attempt to match your fingerprint with the template was not successful.
- If the amber LED flashes slowly and continuously, it is in the biometrics blocked state.
- If the key does not react to your touch, you might not have touched both the bezel and the sensor. When you apply your fingerprint, always make sure you are touching the bezel at the same time. See Tips for the Touch below.
Fingerprint Enrollment Progress Indicators
The progress of reading of your fingerprint is displayed on-screen. The way it is shown depends on the client platform and browser. It is generally not under the control of the site or the service. The screenshots below show enrollment using platform support:
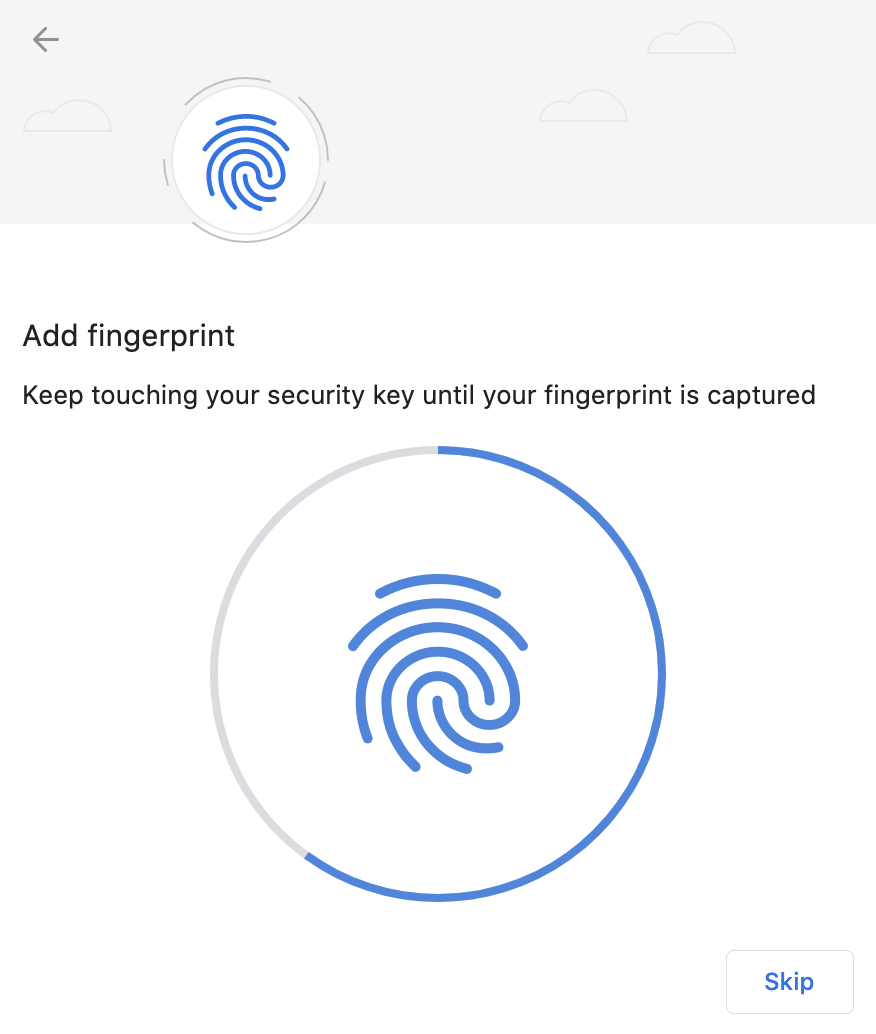
Chrome on macOS, Linux, and Chrome OS: Capturing the Fingerprint

Windows: Capturing the Fingerprint
Fingerprint Orientation
The YubiKey Bio supports 360 degree fingerprint reading, meaning that a fingerprint can be read from any angle once successfully enrolled.
Tips for the Touch
Because the fingerprint can be negatively affected by environmental conditions such as heat, cold, injury, etc., it is not always easy for the YubiKey Bio to interact with it. The following tips are helpful.
The YubiKey Bio recognizes two interactions, one a touch, and the other a fingerprint. Its recognition of the fingerprint - or lack thereof - is communicated through the LEDs. See LED Behavior.
On the YubiKey Bio, the silver-colored bezel encircling the fingerprint sensor provides the grounding plane required to read the fingerprint. Touch types:
| Biometric: | When prompted to have the YubiKey Bio read your fingerprint from the fingerprint sensor, be sure to touch at least a tiny part of the ring. If you use your little finger to touch only the center of the fingerprint sensor, the key does not read the fingerprint. |
|---|---|
| Plain: | When prompted to touch the YubiKey Bio but not explicitly asked for the fingerprint, touch both the bezel and the fingerprint sensor, even though the fingerprint is not read. |
| Fingerprint: | For enrolling, when we say fingertip, we actually mean the pad on the tip of the finger where the whorls of the fingerprint are. The fingerprint could equally well be a thumbprint or a toeprint; the YubiKey Bio makes no distinction between fingers, thumbs, and toes. |
|---|---|
| Print quality: | Dry or scarred skin can impede the key’s ability to perform a successful fingerprint match. If your hands are dry, use moisturizer or water to enable conduction. Do not apply wet fingertips. |
| Repeat reading: | Enrolling your fingerprint requires pressing your fingertip against sensor (and bezel) several times, usually 5 to 8 times. If an attempt to capture is unsuccessful the YubiKey Bio needs you to repeat enrolling. |
| Vary the angle: | When enrolling a new fingerprint, angle your finger so that different parts of the fingerprint come in contact with the sensor and bezel with each capture. This enables the YubiKey Bio sensor to collect a larger area of your finger. |
| Temperature: | If the fingertip is too cold, the YubiKey Bio might not be able to read the fingerprint. If your hands are cold, rub them together to get the circulation going and warm them up. |
| Press firmly: | Press the YubiKey Bio sensor and bezel with your fingertip gently but firmly and hold for a second or so. If you are using an adapter, it may be necessary to hold onto the adapter to prevent it from bending and interrupting the connection to the YubiKey. |
| Stable key: | If the YubiKey Bio seems to wobble in the USB port, use your other hand to hold it steady in the port while you are applying your fingertip. |
| Stable dongle: | If you are using a dongle as an adapter to your device’s USB port, ensure the YubiKey Bio is stable enough for you to apply sufficient pressure with your fingertip. |
| Check the LEDs: | When you start enrolling a fingerprint, the green LED on your YubiKey Bio starts to flash. Start enrolling the fingerprint before the green LED on the YubiKey Bio stops flashing. The amber LED might flash slowly, indicating that no fingerprint is enrolled or that biometrics is in the blocked state. |
| Clean sensor: | If there is dust or oil residue on the YubiKey Bio sensor and bezel, clean it. See Care and Cleaning. |
| Change ports: | Sometimes the USB port does not work well or the YubiKey Bio is loose in the port. Insert the YubiKey Bio in a different port on your device. |
Troubleshooting and Tools
Troubleshooting
The primary source for troubleshooting tips is the FAQ on the YubiKey Bio Series setup page.
| Fingerprint: | If the YubiKey cannot match fingerprint to template three times in a row, fingerprint recognition is blocked. The YubiKey Bio falls back to PIN. |
|---|---|
| PIN: | If you enter the wrong PIN eight times in a row, the YubiKey FIDO2 application becomes locked, which means it cannot communicate with you or with any site or service. It indicates the blocked state by flashing its amber LED slowly and continuously. In order to restore this functionality, reset the FIDO2 application. For more details, see FIDO2 PIN. |
| Unblock: | To unblock the YubiKey Bio’s biometric function (its ability to read fingerprints) by using any of the following:
|
If you run into any issues with a YubiKey Bio, you can also refer to the Knowledge Base on Yubico’s Support site and search for your issue. If your issue is not listed in the Knowledge Base, or if you have any technical questions, you can open a ticket with our Technical Support team.
Unblocking/Unlocking
| Fingerprint: | If the YubiKey cannot match fingerprint to template three times in a row, fingerprint recognition is blocked. The YubiKey Bio falls back to PIN. |
|---|---|
| PIN: | If you enter the wrong PIN eight times in a row, the YubiKey FIDO2 application becomes locked, which means it cannot communicate with you or with any site or service. It indicates the blocked state by flashing its amber LED slowly and continuously. In order to restore this functionality, reset the FIDO2 application. For more details, see FIDO2 PIN. |
| Unblock: | To unblock the YubiKey Bio’s biometric function (its ability to read fingerprints) by using any of the following:
|
For resetting, see Resetting.
Other Issues
If you run into any issues with a key from the YubiKey Bio Series, refer to the Knowledge Base and search for your issue. If your issue is not listed in the Knowledge Base, or if you have any technical questions, you can get in touch with Yubico Support, http://yubi.co/support.
Tools
Yubico Authenticator
The Yubico Authenticator tool can be used to manage the YubiKey Bio. It is open source and cross-platform, running on Windows, macOS, and Linux. Note that the iOS and Android versions of Yubico Authenticator cannot be used to manage the YubiKey Bio.
Click for Yubico Support.