Home
Important
The Home feature is available for Yubico Authenticator for Desktop and Android only.
The Home page is the main hub of the Yubico Authenticator app. It provides an overview of each connected YubiKey as well as general YubiKey management functionality, including the ability to:
- switch between multiple connected keys
- customize a YubiKey’s label and color in the app
- toggle YubiKey applications on/off
- perform a factory reset of a YubiKey application
The Home page: YubiKey at a glance
The Home page displays a wealth of important information about the connected YubiKey, including:
- YubiKey model (e.g. YubiKey 5 NFC).
- Custom label (if one was created).
- Serial number.
- Firmware version.
- PIN complexity status (available for YubiKeys with the PIN complexity feature only).
- Enabled applications for current connection type (USB or NFC). Applications include Yubico OTP, PIV, OATH, OpenPGP, FIDO U2F, FIDO2, and YubiHSM Auth, depending on your YubiKey.
- FIPS status (available for YubiKey 5 FIPS Series keys with firmware 5.7 or later).
PIN complexity status
PIN complexity is a new feature offered with firmware version 5.7. If PIN complexity is enabled, the YubiKey will block the usage of trivial PINs, such as “11111111”, “password”, or “12345678”.
If the feature is enabled on your key, you will see the PIN complexity status (“PIN complexity enforced”) on the Home screen, which is underneath the firmware version. PIN complexity enablement occurs during YubiKey manufacturing and cannot be modified (disabled or re-enabled) via Yubico Authenticator.
PIN complexity is enabled by default on select YubiKey series and available as an optional add-on for some custom-configured YubiKeys. For more information on the PIN complexity feature and the full PIN blocklist, see the YubiKey Technical Manual. To verify PIN complexity support for various the YubiKey series, see the Firmware 5.7 Capabilities table.
Note
Yubico offers custom configuration options to personalize YubiKeys during production. For more details, visit Yubico’s Customization guide.
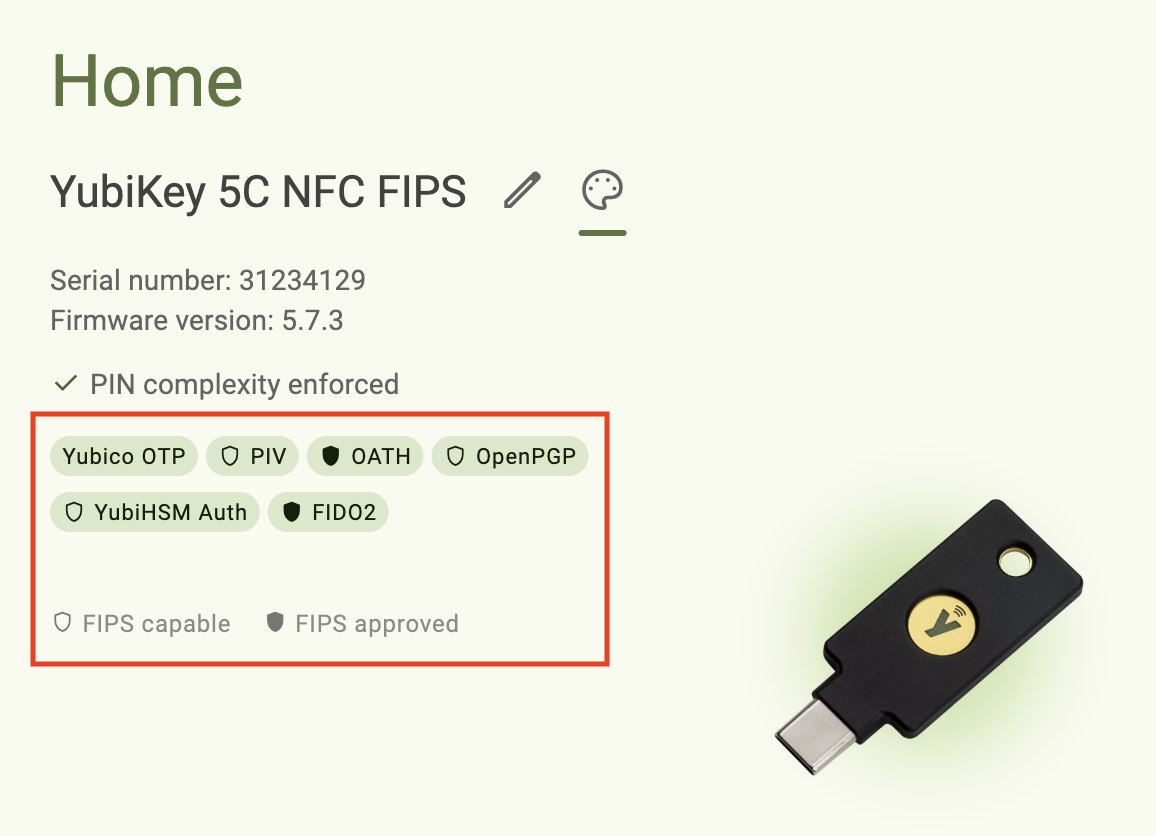
FIPS status
The FIPS status, which is available for YubiKey 5 FIPS Series keys with firmware 5.7 or later, has two components: FIPS capable and FIPS approved.
“FIPS approved” refers to YubiKey applications that are in compliance with the FIPS 140-3 standard. “FIPS capable” refers to YubiKey applications that are capable of complying with FIPS 140-3 but haven’t yet been configured to achieve that status.
Note
For a complete list of the YubiKey requirements for FIPS 140-3, see the YubiKey Technical Manual.
The following YubiKey applications are capable of FIPS 140-3 compliance:
- PIV
- FIDO2
- OATH
- OpenPGP
- YubiHSM Auth
To check a key’s FIPS status, look for the FIPS shield icon next to the application name on the Home screen. If an application has been disabled, you must re-enable it to check its FIPS status.
Yubico Authenticator will not allow you to create credentials for applications in the FIPS capable state. This includes OATH accounts, FIDO2 passkeys, and PIV keys and certificates. The Yubico OTP application, which cannot be in the FIPS capable or FIPS approved states, is unaffected.
Once an application transitions to the FIPS approved state, the only way to return to the FIPS capable state is by performing a factory reset of that application.
Note
Yubico Authenticator for desktop and Android support Secure Channel Protocol 11b (SCP11b). This ensures that NFC connections between the app and YubiKey 5 FIPS Series keys are FIPS-compliant as long as the device running Yubico Authenticator also supports AES-CMAC (native support for AES-CMAC on Android is version-dependent).
Putting an application in FIPS approved mode
The PIV, FIDO2, and OATH applications can be put into the FIPS approved state using Yubico Authenticator. Once an application is in the FIPS approved state, you will have full access to the application’s functionality.
Do the following for each application:
- OATH
- Set an OATH application password.
- FIDO2
- Set a FIDO2 PIN. The PIN must be at least 8 characters and adhere to the key’s PIN complexity requirements.
- PIV
- Change the PIV PIN and PUK. They must be at least 8 characters and adhere to the key’s PIN complexity requirements.
- Change the Management Key. You must use an AES key algorithm, which will be automatically enforced by Yubico Authenticator.
Note
The YubiHSM Auth and OpenPGP applications cannot be put into FIPS approved mode with Yubico Authenticator. (In fact, the only YubiHSM Auth and OpenPGP functionality the Authenticator offers is the ability to toggle those applications on/off.) To interact with these applications, use the ykman CLI tool. For more information on the requirements that must be met for the YubiHSM Auth and OpenPGP applications to achieve FIPS approved status, see the YubiKey Technical Manual.
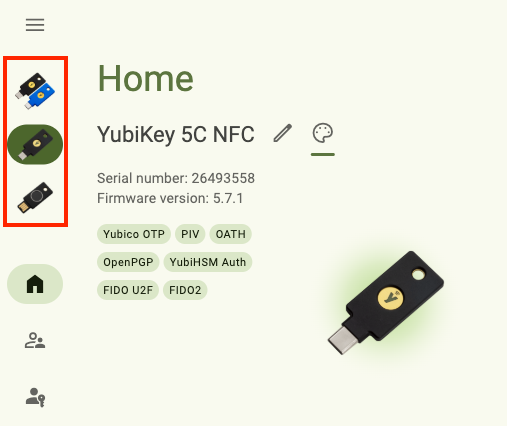
Switch between keys
Note
Toggling between multiple connected YubiKeys is available on Yubico Authenticator for Desktop only.
Yubico Authenticator for Desktop allows you to interact with multiple connected YubiKeys (only one key can be connected over NFC, but USB connections are not limited). When performing operations in Yubico Authenticator, changes can only be applied to one key at a time.
If you have more than one YubiKey connected to your desktop device, you can toggle between them by selecting a key underneath the menu icon in the upper left corner of the app. Any YubiKey changes made via the Home, Accounts, Passkeys, Fingerprints, Certificates, and Slots pages will apply to the selected key only.
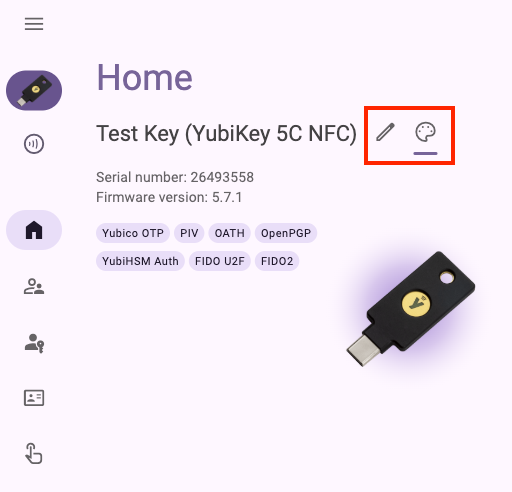
Change a YubiKey’s label and color
By default, connected YubiKeys are labeled with their model name on the Home page and the left menu bar. They also have a default color scheme within the app (green on desktop, purple on Android).
To assist with managing multiple keys, key labels and colors can be customized. When a custom label is created, the key’s model name is moved into parentheses after the custom text. These changes persist on the device they are initiated on; if a key is unplugged and then reconnected, the label and color will reflect whatever was previously configured. If multiple keys with different colors are connected to your desktop device, switching between them will change the app’s color scheme.
The label and color information is stored in the app itself, not on the YubiKey. If you toggle these settings for a key on Device A and then connect the key to Device B, you will not see the label/color changes in the app on Device B.
To change a label or color for a particular YubiKey, do the following:
Plug your YubiKey into your device, click on the left menu icon in the upper left corner of the app and select Home.
To connect via NFC on desktop, click the NFC icon in Yubico Authenticator and place your YubiKey on top of a desktop NFC reader. The key must maintain constant contact with the reader throughout the operation.
To connect via NFC on Android, tap your YubiKey on the back of your device to scan.
To change the color, click the palette icon and select a new color.
To change the label, click the pencil icon next to the key’s model name. Enter a new name for your key and click Save.
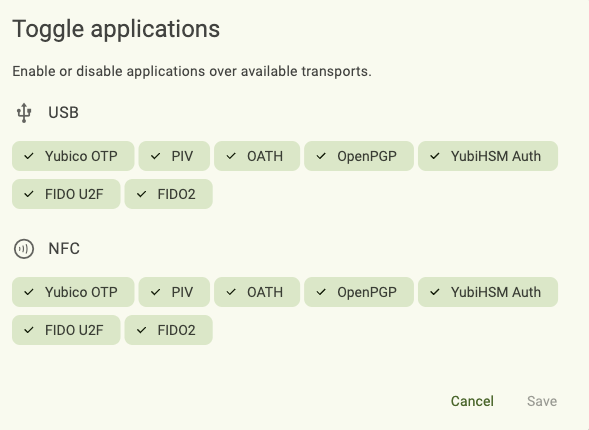
Toggle YubiKey applications on/off
The YubiKey applications, which include Yubico OTP, PIV, OATH, OpenPGP, FIDO U2F, YubiHSM Auth, and FIDO2, can be enabled or disabled for both USB and NFC connections. If an application is disabled, that application will no longer interact with connected devices over the indicated connection type.
For example, if the Yubico OTP application is disabled over USB, the key will no longer emit a Yubico OTP (if a slot is configured with one) when the key is connected to a device over USB and touched. If the Yubico OTP application is disabled over NFC, it is not possible to start Yubico Authenticator for Android on an NFC tap.
A caveat: you cannot disable all applications over USB. Additionally, on Android, the OTP application cannot be the only application enabled over USB (the YubiKey would become impossible to detect on Android otherwise).
For YubiKey Bio Multi-protocol Edition keys, once the key is considered “in use”, applications cannot be toggled on/off until a factory reset is performed. “In use” means that the key has been configured in some way: a PIN has been set, the PIV management key has been changed, a certificate has been loaded into one of the PIV application slots, etc.
Note
Enabling/disabling an application does not reset the application; all credentials and settings are preserved.
To enable/disable an application, do the following:
Plug your YubiKey into your device, click on the left menu icon in the upper left corner of the app and select Home.
To connect via NFC on desktop, click the NFC icon in Yubico Authenticator and place your YubiKey on top of a desktop NFC reader. The key must maintain constant contact with the reader throughout the operation.
To connect via NFC on Android, tap your YubiKey on the back of your device to scan.
Click Toggle applications under DEVICE. To find the DEVICE menu in a narrow app window, click the right menu icon in the upper right corner.
To enable an application, click on it until it shows a check mark. To disable an application, click on it until the check mark disappears. When you are done, click Save.
For NFC connections on Android, scan your key when prompted to confirm the operation.
Reset a YubiKey application to its factory default state
The FIDO2, OATH, and PIV applications can be reset to their factory default states via the Home page in Yubico Authenticator for Desktop and Android. For more information on what a reset entails and how to prepare for and perform a reset, see the Factory Reset chapter.