Factory Reset
With the help of Yubico Authenticator, the YubiKey can be reset to factory default settings by application.
Depending on the YubiKey model and platform, this can include the FIDO2, OATH, and PIV applications. For all YubiKey models except for the YubiKey Bio Series Multi-protocol Edition (MPE), if one application is reset, the others are not affected.
Note
YubiKey Bio Series Multi-protocol Edition (MPE) keys share a PIN between the PIV and FIDO2 applications. Therefore, a reset affects both applications.
Once an application is reset, the operation cannot be undone.
What happens during a reset?
When the FIDO2 application is reset, Enterprise Attestation (available with custom-configured keys only) is disabled, and the FIDO2 PIN and all fingerprints, passkeys, and non-passkey FIDO2 credentials are removed from the YubiKey. Similarly, when the OATH application is reset, all OATH account credentials plus the OATH application password are removed.
When the PIV application is reset, all private keys and certificates are removed from the YubiKey, and the PIN, PUK, and management key are reset to their factory default values.
The Yubico OTP application itself can’t be reset, but the configuration of each slot can be deleted. See Slots: Yubico OTP Application for instructions on how to perform this operation.
Note
For YubiKey 5 FIPS Series keys with firmware version 5.7 or later, a reset will return all “FIPS approved” applications back to the “FIPS capable” state.
How does a reset affect my accounts?
While a reset removes credentials from the YubiKey, it does not affect the accounts and services that those credentials are registered with.
For example, suppose you registered a YubiKey for OATH authentication with your GitHub account. If you reset the OATH application on your key, the OATH credentials linked to your GitHub account will be removed from the key, but if you log into your GitHub account, you’ll still see the key registered for two-factor authentication in your settings. However, you will not be able to authenticate to your account using that key because it no longer has the corresponding OATH credentials. To use the key with that account again, you will have to reregister it.
Recommended preparation
Prior to performing a reset, we recommend that you either register a backup YubiKey or temporarily disable two-factor authentication with each account that will be affected by the reset. This ensures that you will still be able to access those accounts once your key is reset.
For passkey and OATH credentials, you can view a list of registered accounts in Yubico Authenticator by going to the Passkey and Accounts screens, respectively.
Performing a reset on desktop and Android
To reset an application, do the following:
Plug your YubiKey into your device, click on the left menu icon in the upper left corner of the app, and select Home.
To connect via NFC on desktop, click the NFC icon in Yubico Authenticator and place your YubiKey on top of a desktop NFC reader. The key must maintain constant contact with the reader throughout the operation.
To connect via NFC on Android, tap your YubiKey on the back of your device to scan.
Select Factory reset under DEVICE.
To find the DEVICE section in a narrow app window, click on the right menu icon in the upper right corner of the app.
In the Factory reset window, select the application you’d like to reset and click Reset. For NFC connections on Android, tap your key to scan when prompted.
YubiKey Bio Series Multi-protocol Edition (MPE) keys share a PIN between the PIV and FIDO2 applications. Therefore, a reset affects both applications. You cannot select an application to reset individually for Bio Series MPE keys.
Also note that custom-programmed YubiKeys with firmware version 5.8 and above may have the “blocked transports” feature enabled, which restricts FIDO2 reset to specific transport types (USB, NFC, Lightning). If enabled, the app will indicate which transports are available for performing a FIDO2 reset.
For OATH and PIV resets, once the operation is complete, the app will automatically return to Home.
For FIDO2 application resets over USB connections, unplug your YubiKey, reinsert your key into your device, and touch your key when prompted (for YubiKey Bio Series keys, touch the fingerprint sensor; for all other keys, touch the gold contact). Once the status reads “FIDO application reset”, click Close on desktop or the X on Android to return to Home.
Note
Custom-programmed YubiKeys with firmware version 5.8 and above may have the “long touch for reset” feature enabled, which requires a touch of at least 5 seconds in duration when resetting the FIDO2 application. The app will indicate the long touch requirement if enabled.
For FIDO2 application resets over NFC connections on desktop, remove your key from the NFC reader and place it back on the NFC reader when prompted. Once the status reads “FIDO application reset”, click Close to return to Home.
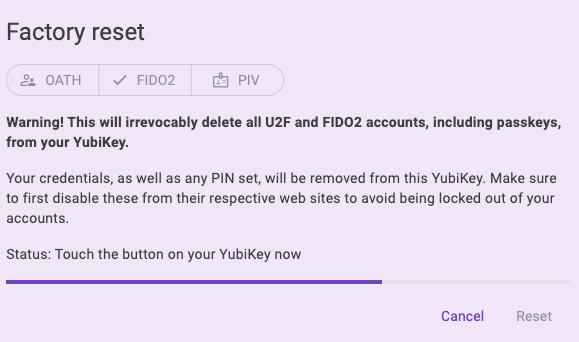
Once the key has been reset, you must reregister it with your accounts to continue using it for authentication with those sites and services.
Performing a reset on iOS/iPadOS
For Yubico Authenticator for iOS, only the OATH and FIDO2 applications can be reset. In addition, FIDO2 reset on iOS is limited to NFC connections for YubiKeys with a firmware version prior to 5.7.4. iPads do not have built-in NFC readers, therefore, only OATH reset is supported on iPadOS at this time. To perform a reset for one of these applications on your iOS/iPadOS device, do the following:
Open the Yubico Authenticator app. For Lighting connections, plug in your YubiKey. For NFC connections, swipe down on the screen and tap your YubiKey on the back of your device to scan.
Note
Lightning is currently the only supported physical connection type for iOS and iPadOS devices. NFC wireless connections are supported on iOS but not on iPadOS. For a complete breakdown of Yubico Authenticator functionality by platform and connection type for each YubiKey model, see the Yubico Authenticator Functionality table.
Click the three dots in the upper right corner of the app and select Configuration.
To reset the OATH application, select Reset OATH application under the OATH section. Click Reset OATH followed by Reset to confirm the operation. For NFC connections, scan your key when prompted.
To reset the FIDO2 application on iOS (NFC connections only for YubiKeys with a firmware version prior to 5.7.4), select Reset FIDO application under the FIDO section. Click Reset FIDO followed by Reset to confirm the operation. Scan your key when prompted.
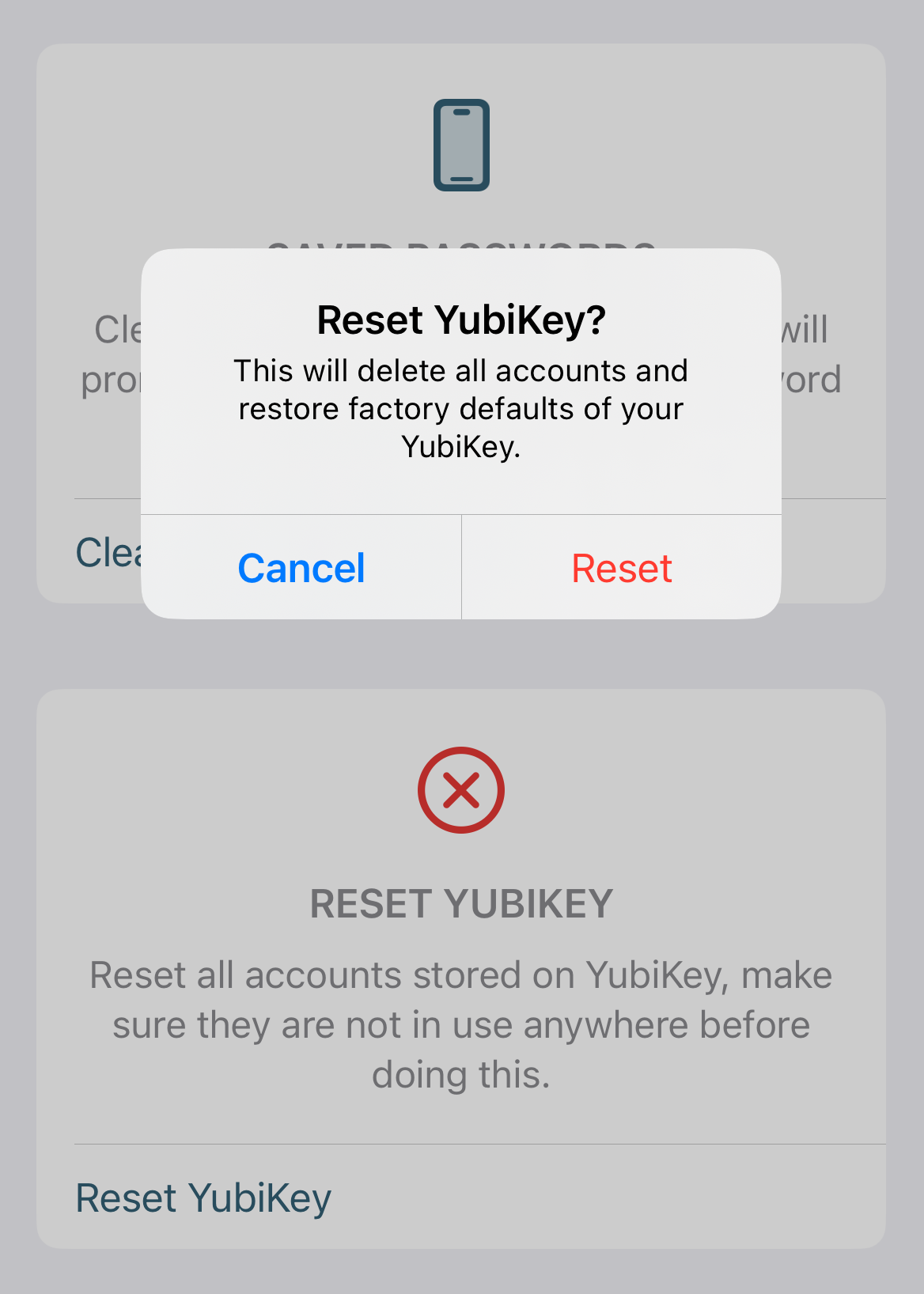
Once the key has been reset, you must reregister it with your accounts to continue using it for authentication with those sites and services.