Tips
The following tips and tricks can help you take full advantage of the Yubico Authenticator application’s functionality:
- Resize the app window on desktop and Android tablets to your preferred size.
- Register spare YubiKeys with your accounts to maintain access in the event of a loss of your primary YubiKey.
- Start Yubico Authenticator with the app window hidden to reduce desktop clutter.
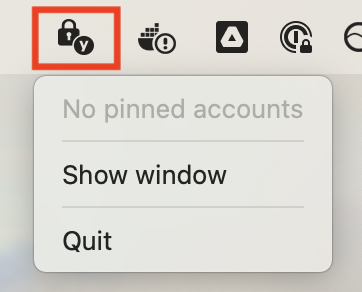
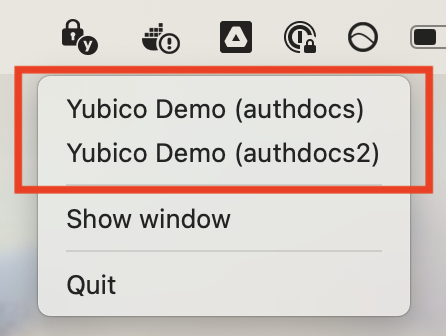
- As a convenient shortcut, generate OATH OTPs from pinned accounts via the menu bar or system tray on desktop devices.
- Set an OATH application password to add an additional layer of security.
- Speed up Yubico Authenticator operations with the help of keyboard shortcuts
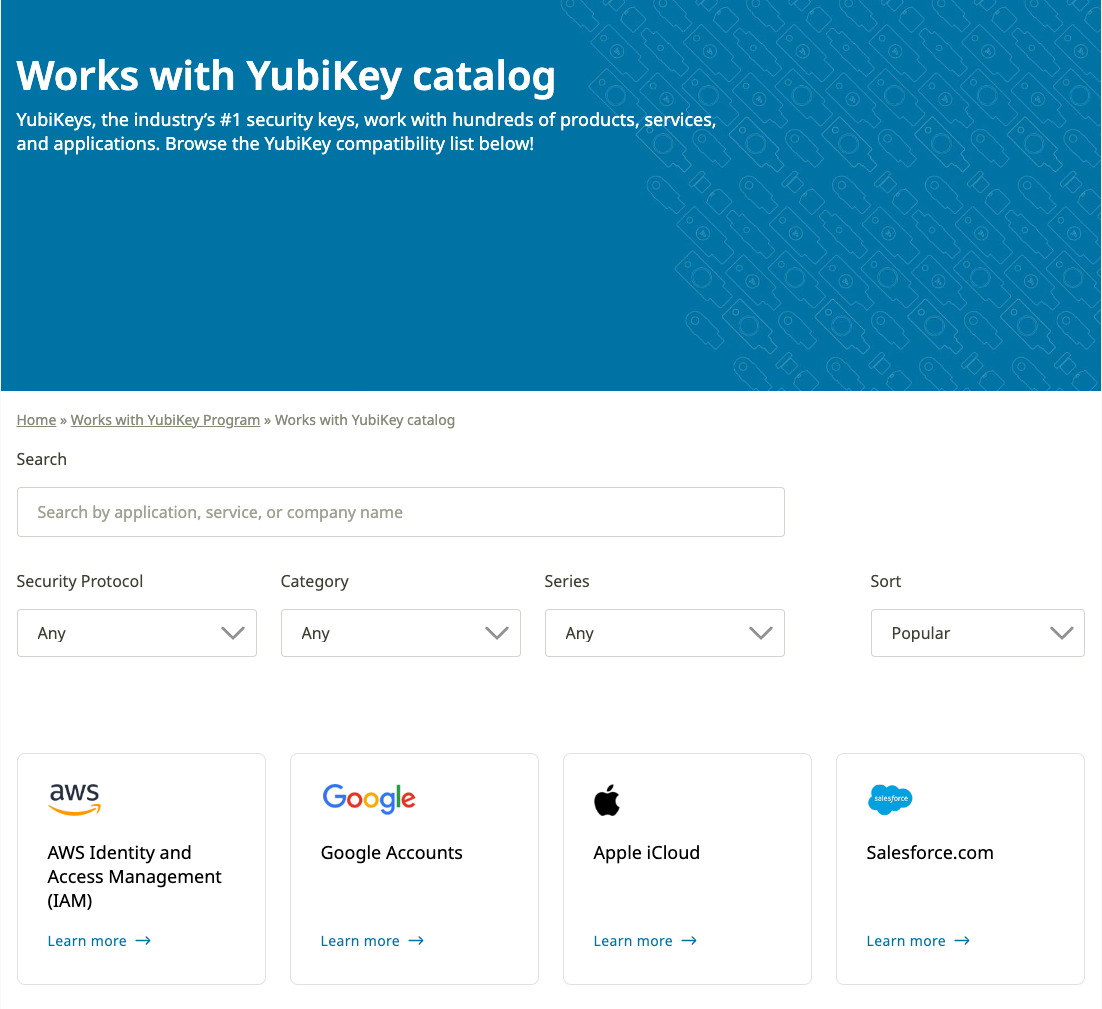
- Check out the Works with YubiKey Catalog for compatibility information (by YubiKey model, security protocol, and site/service/account) and account setup information.
Resize the app window
Note
The app window size can only be changed on desktop and Android tablet devices.
The Yubico Authenticator app window can be resized by both height and width. The default window width on most desktop devices shows the following:
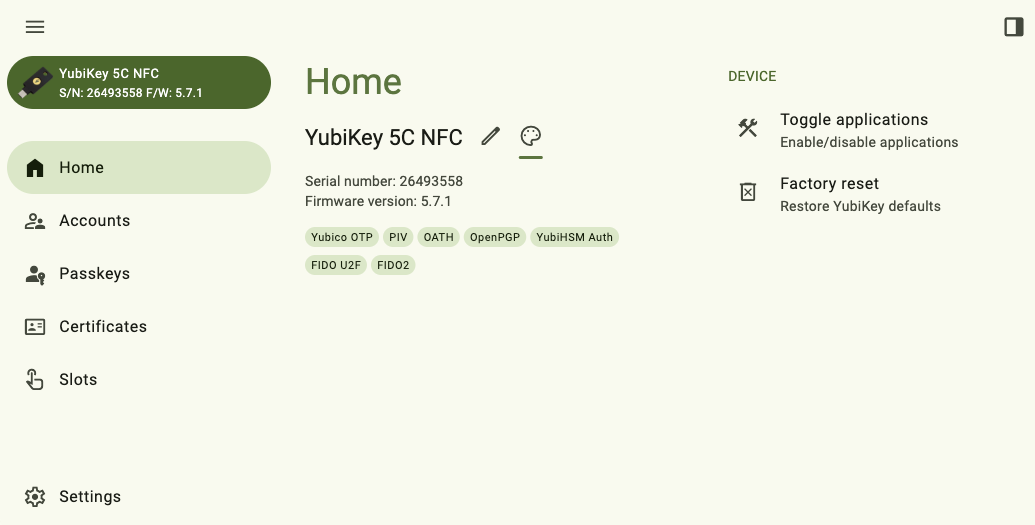
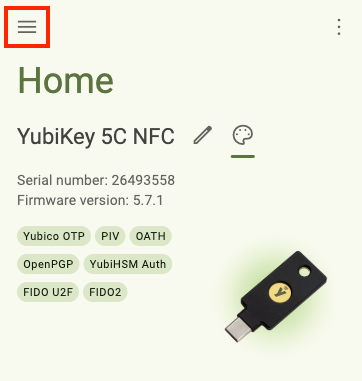
When the window is narrowed sufficiently, only the icons for the left-hand menu items are shown. To view the full icon text (page titles and YubiKey information), click on the left menu icon in the upper left corner of the app:
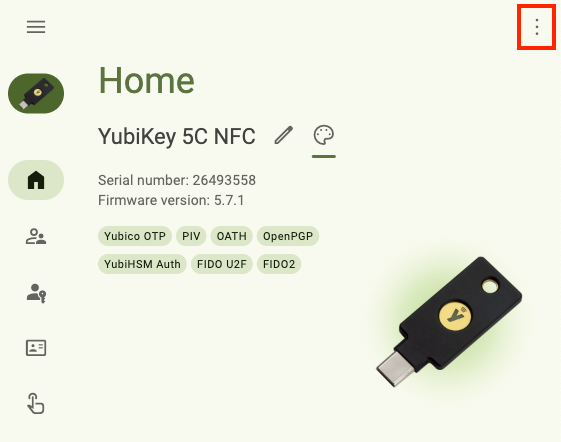
Narrowing the window again hides the right-hand menu. However, these menu options can still be accessed by clicking on the right menu icon in the upper right corner of the app:
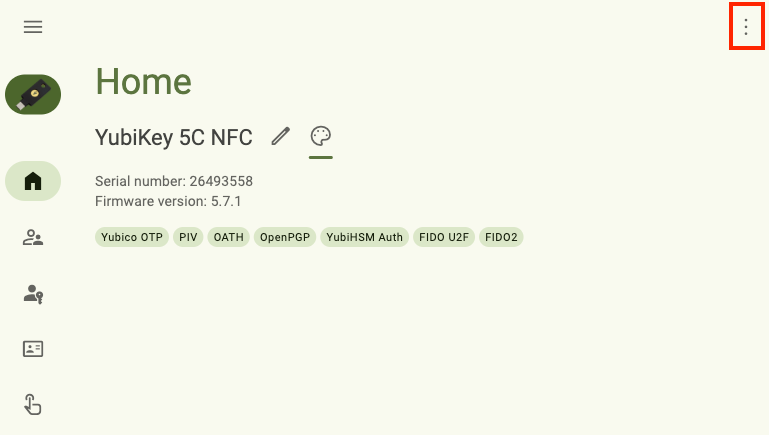
Further narrowing the width makes all page icons disappear. However, these pages can still be accessed by clicking on the left menu icon in the upper left corner:
When the window is fully widened, all menu items are expanded. To collapse the left-hand menu items, click on the left menu icon in the upper left corner. To collapse the right-hand menu items, click on the right menu icon in the upper right corner. Click the icons again to re-expand.

Change the Accounts and Passkeys screen layouts
Note
The Passkeys and Accounts screen layouts can only be changed on desktop and Android devices.
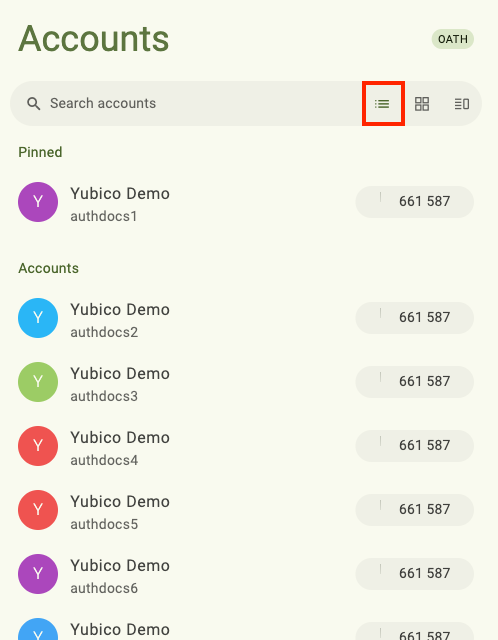
If you have a lot of passkeys or OATH accounts on your YubiKey, it may not be possible to see them all in Yubico Authenticator without scrolling when using the default List layout:
However, desktop and Android tablet devices can take advantage of a wider screen by using the Grid layout:
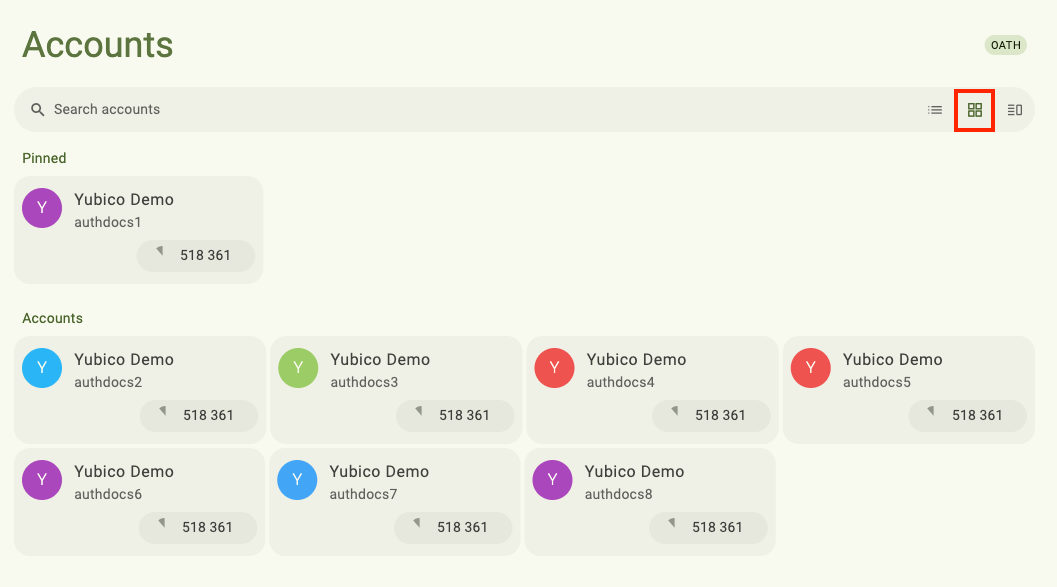
Or for the best of both worlds, try the Mixed layout (available for the Accounts screen only and requires that at least one account be pinned):
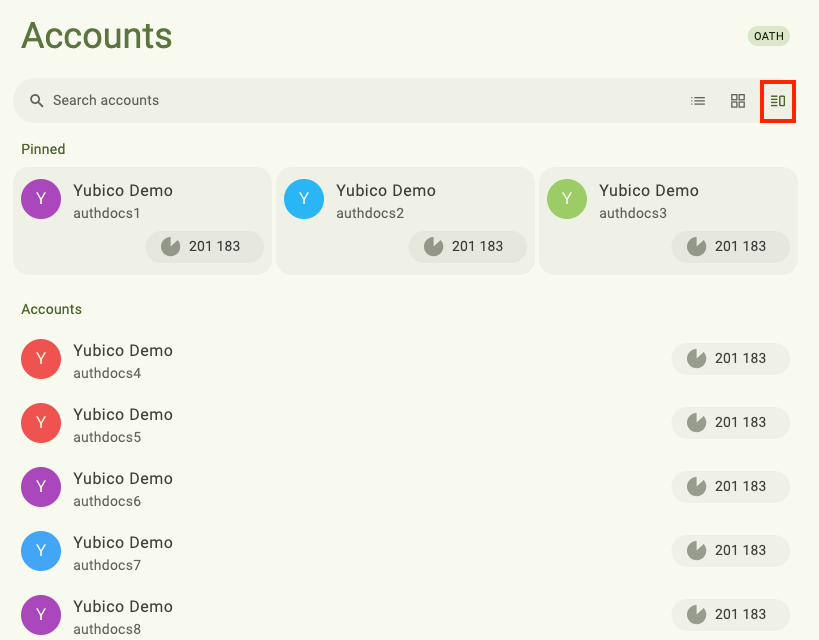
Toggle between the layout options on the Accounts and Passkeys screens by selecting the desired layout icon in the search bar.
Register a spare YubiKey
We highly recommended registering at least one backup YubiKey with each account you have. In the event that you lose your primary YubiKey, you will still be able to access your accounts with your spare key.
The registration process for the spare key depends on the type of authentication and the specific site/service. Refer to the following sections.
OATH accounts
To register a spare YubiKey for OATH authentication, the OATH account must be added to the spare key using the same QR code and credentials as your primary key. This means that the primary key and spare key will generate the same TOTP codes in Yubico Authenticator on any device.
For many sites and services, OATH authentication is often referred to as “registering an authenticator app” in your account settings. Generally, these sites/services allow you to register only one application, meaning that only one set of OATH credentials can be associated with your account at a time. So to be able to use more than one YubiKey to generate TOTP codes in Yubico Authenticator for a single account, each of those keys must have the same credentials so that they can generate the same TOTPs.
If you do not have a copy of the QR code or OATH credentials used to register your primary key, you will have to remove your primary key from your account and reregister the primary key along with the spare key. To do so, perform the following:
- Locate the OATH authentication settings within your account. For guidance on how to find this with your particular site/service, see the Works with YubiKey catalog.
- Remove the registered key/app and generate a new QR code or OATH credentials. Take a screenshot of the QR code or copy the OATH credentials.
- Perform the full registration process for the primary key.
- Register the account with the spare key in Yubico Authenticator using the screenshot of the QR code or copy of the OATH credentials. You do not need to provide another TOTP to the site/service in order to complete the registration process; once your primary key has been successfully registered, spare keys need only to be configured in the Yubico Authenticator app.
- Once completed, you should see the keys generate the same TOTP codes in the Yubico Authenticator app. As a security best practice, delete the QR code screenshot or copy of the OATH credentials once all spare keys have been registered.
Passkeys
To register a spare YubiKey for use as a passkey with an existing account or service, follow the same steps you performed when registering your primary key. See the Works with YubiKey catalog for more information on your account’s specific registration process.
Yubico OTP application credentials
Spare YubiKeys can be configured for all Yubico OTP application configuration types:
- Yubico OTP
- Challenge-response
- Static password
- OATH HOTP
Yubico OTPs
For sites and services that use Yubico OTP authentication, register a spare key the same way that you registered the primary key. See the Works with YubiKey catalog for more information on your account’s specific registration process.
An important caveat: if the site/service in question uses the YubiCloud validation service and the Yubico OTP credential on your spare key has not been registered with YubiCloud, you will need to do that prior to registering the key with the site/service. To register a Yubico OTP credential with YubiCloud, upload the required information via the Yubico OTP key upload form. You will need the key’s serial number, public ID, private ID, and secret key.
How do you know if your Yubico OTP credential is registered with YubiCloud? Generate and submit a Yubico OTP with your key for validation on the Yubico demo site. As a reminder, tap the key briefly to active the short press slot or touch and hold the key to activate the long press slot.
Note
Standard YubiKeys are preconfigured with a Yubico OTP in the short press slot. This credential is also preregistered with YubiCloud for out-of-the-box validation.
If the site/service uses a non-YubiCloud validation server, the OTP credential information (serial number, public ID, private ID, and secret key) will need to be shared with the server during the registration process.
Challenge-response credentials
To register a spare YubiKey for challenge-response authentication, you must configure a slot of the spare YubiKey with the same challenge-response secret key as your primary key.
If you do not have a copy of the secret key that the primary key was configured with, you will have to reconfigure and reregister the primary key in addition to configuring the spare key.
Static passwords
To register a spare YubiKey for static password authentication, you must configure a slot of the spare YubiKey with the same static password and keyboard layout as your primary key.
If you do not remember your static password, open a text editor and activate the slot on your primary key that is configured with the static password (tap the key briefly to active the short press slot or touch and hold the key to activate the long press slot). The static password will be typed into the text editor.
If you do not remember the keyboard layout the primary key was configured with, you will have to reconfigure and reregister the primary key in addition to configuring the spare key.
OATH HOTP
To register a spare YubiKey for OATH HOTP authentication, you must configure a slot of the spare YubiKey with the same OATH HOTP secret key and OTP length as your primary key.
If you do not have a copy of the secret key that the primary key was configured with, you will have to reconfigure and reregister the primary key in addition to configuring the spare key.
If you do not remember the OTP length that the primary key was configured with, open a text editor and activate the slot on your primary key that is configured with the OATH HOTP credential (tap the key briefly to active the short press slot or touch and hold the key to activate the long press slot). The HOTP will be typed into the text editor. Count the number of digits present; this is the OTP length.
Set an OATH application password
Note
OATH-compatible YubiKeys include the YubiKey 5 Series (standard, FIPS, and CSPN), YubiKey 4 Series, and YubiKey NEO.
To further enhance the security of your YubiKey, create a password for its OATH application. Once the OATH application has password protection, the key’s OATH accounts and their OTPs cannot be viewed or generated until the correct password is entered in the Yubico Authenticator app.
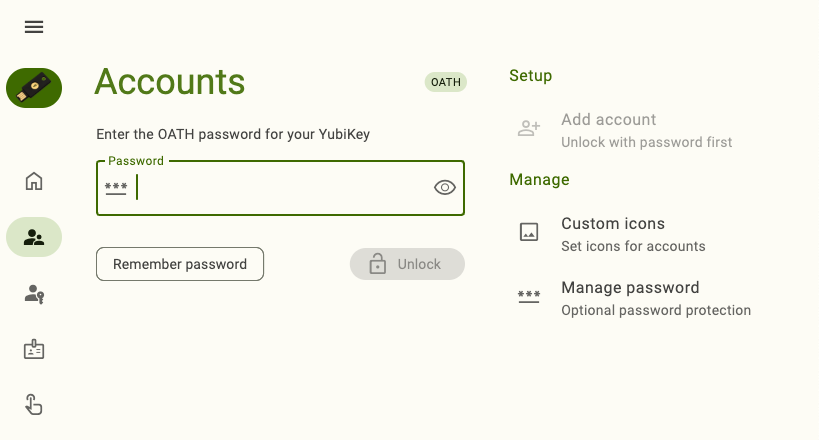
To create and manage an OATH password, see the OATH Accounts chapter.
Keyboard shortcuts
Note
Keyboard shortcuts are fully supported on Yubico Authenticator for Desktop only.
Take advantage of the available keyboard shortcuts to speed up operations such as calculating OATH codes, toggling through connected YubiKeys and menu items, and hiding the app.
Top view the full list of keyboard shortcuts within Yubico Authenticator, go to Settings, select Help and about, and click on Keyboard shortcuts under the HELP section.
Operation
|
Shortcut
(macOS)
|
Shortcut
(Windows)
|
|---|---|---|
| Open Keyboard shortcuts help screen | Cmd + / | Ctrl + / |
| Expand/collapse left menu | Cmd + B | Ctrl + B |
| Expand/collapse right menu | Option + Cmd + B | Alt + Ctrl + B |
| Open Search (if available) | Cmd + F | Ctrl + F |
| Dismiss/close | Escape | Escape |
| Next YubiKey | Ctrl + Tab | Ctrl + Tab |
| Previous YubiKey | Ctrl + Shift + Tab | Ctrl + Shift + Tab |
| Open Help and about | F1 | F1 |
| Hide Yubico Authenticator | Cmd + W | Ctrl + W |
| Quit Yubico Authenticator | Cmd + Q | Not supported |
| Open Settings | Cmd + , | Not supported |
| Calculate OATH code | Cmd + R | Ctrl + R |
| Copy OATH code to clipboard | Cmd + C | Ctrl + C |
| Navigate within Yubico Authenticator | Arrow keys | Arrow keys |
| Open item details | Return or Space | Enter or Space |
| Delete item | Delete | Delete |
Works with YubiKey Catalog
Not sure if a particular site or service supports a specific security protocol or YubiKey model? Check out the Works with YubiKey Catalog to quickly and easily find compatibility information.